Overview:
- Assess likely risks of the system and specific cost by analysing the requirements and design.
- Identify drawbacks or improper security requirements.
- System operation security.
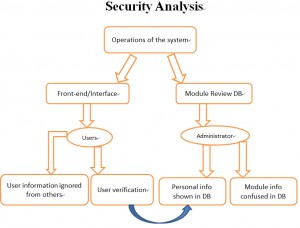
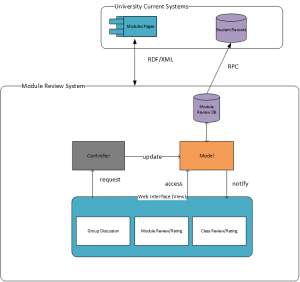
For LessonPlan 2.0, as it is a social media platform for module reviews, the effective operation of the system is extremely important and the main secure factors are about the design and structure of the system, including the database that used to store the useful and updated information. The detailed contents of the system architecture design were posted by one of our group members (AHMED AL-BRASHDI) on April 27, 2015. Here is the flow chart of security analysis.
Actually, the main security analysis of the system will focus on the technology. The system can be divided into two parts: Front-end and Backend. For the Front-end, normally, the system can be used in a public network, such as the computer room in university, when one student log in the system successfully, the second one can not enter it when using the computer that has the same IP address, so the second one will not view the status of the module option for the previous. This is one point about users’ interaction.
For the Module Review Database, as the related information of modules is too much and it may cause confusion between several modules, such as the module leader, module place, module time, etc. Managing well the database is very essential for the system operates in a correct way.
Since the system has a login and user profile information, we think about how to overcome any vulnerabilities associated with each page.
As a web application, the main possible vulnerabilities as in OWASP top ten 2013 [1]:
1- Injection: will focus more on SQL Injection here. The login form and any other form has to prevent such attach. The danger comes when the attacker can trick sql statement and gets over authentication and authorization. He /she can then login as an admin and harm the entire application or database. Also, injecting delete or drop sql statement will remove table records or remove the entire table with its structure and definition. To overcome this, we should use parametrized interface or statement like using PrepareStatement in JDBC. Another way is to escape special characters using DBMS. Third option is to use stored procedure instead.
2-Cross-Site Scripting: if the user input has not been escaped correctly, the site might be vulnerable to cross-site scripting. To overcome this, we need to escape all untrusted data and use libraries like OWASP’s AntiSamy.
The other vulnerability might not have the same weight as these main two in LessonPlan 2.0. However, the proper prevention strategy will be applied in all of them to ensure the highest security possible. This include hashing session ids, using secure HTTP and hashing user password [2].
——–
[1] The OWASP Foundation, “OWASP Top 10 for 2013″, 2013
[2] Provided by Ahmed Al-Brashdi, 2015