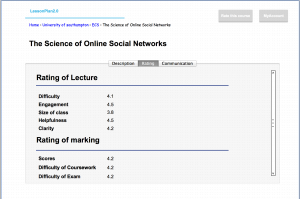
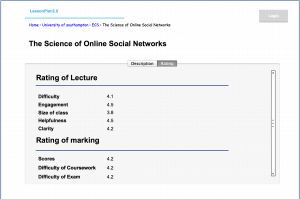
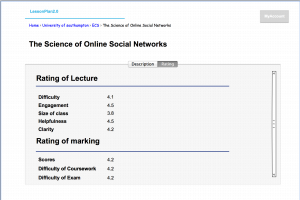
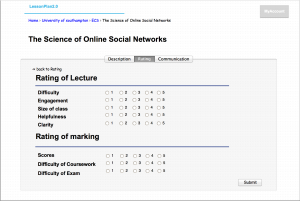
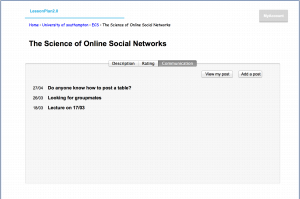
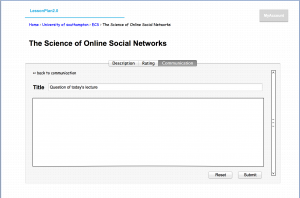
Version 1 of ‘LessonPlan’ will be released as a full functioning platform, but due to time constraints more advanced features will be implemented in future versions.
Some of the planned features are detailed below. The extra features simplify and make more robust some of the functionality of the platform, but all said functionality is completely operational in version 1 without them.
- Suggestion algorithm
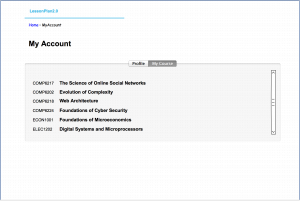
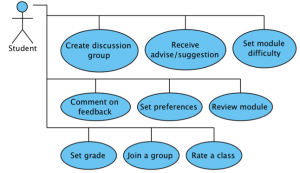
One of the main goals of ‘LessonPlan’ is to facilitate module selection, allowing students to make more informed choices when selecting optional modules. This is based on the premise that providing students with information apart from the limited details of the module overview pages – and especially feedback on the practical applications of the module descriptions – will allow them to have a clearer picture of the module’s learning outcomes and requirements. In the initial release of the platform this is largely based on the inferences that each student can make from the feedback, comments and discussions that other students have posted. Implementing a suggestion algorithm would offer some automation on this task: The algorithm will be able to notice patterns in module selection and relate them to satisfaction. It will then be able to offer those observations as suggestions. For example, if a student A has rated Module X and Module Y as very interesting in Semester 1, and rates Module Z as very interesting in Semester 2, there’s a probability that students that have also found Modules X and Y interesting will have an interest in Module Z as well.
- Posts’ ratings
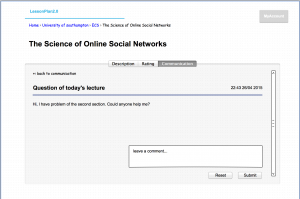
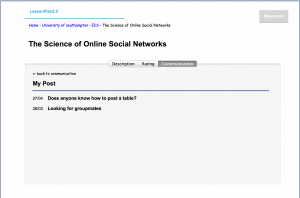
As detailed in the post about Trust here, implementation of ratings for comments and discussion posts is intended in the future. This would allow users to up-vote a post that they found particularly helpful, useful or interesting. That would provide new users with an instant indication about the validity of the post, while encouraging users to post more responsibly.
- Flags for abusive content
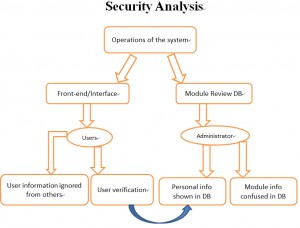
For the initial release of ‘LessonPlan’ it was decided that no active monitoring or moderation of posts was needed to keep content clean and clear. From studies of Graph Theory on Online Social Networks it has been noted that an accentuated characteristic of a network shapes the behaviour of its members. Since members of the platform will be University students, with their credentials logged into the system, it is a safe assumption that the majority of them will behave ethically, in line with the Acceptable Use policies. This then, as a network effect, constrain potentially deviant behaviour from other members. This assumption is re-enforced by what is detailed in the post about Trust: Where social capital and trust exist, members can rely on informal fairness rather than constant active monitoring and exhausting rules of provenance.
Nevertheless, future versions of ‘LessonPlan’ can address this issue if need be. The feature will allow users to flag up abusive posts. Posts that gather a certain amount of flags, will be marked for inspection. And after a certain amount of flagged up posts, prevention policies could be set in place (for example, warnings, suspension or even deletion from the system).