Goodbye, #UOSM2033!
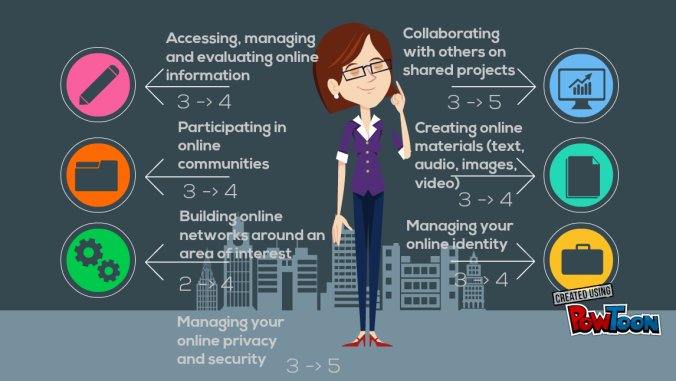
As a year-3 psychology student, UOSM2033 actually took me by surprise as it unlike any other modules that I have studied before. Even so, I am glad that I made this attempt, as this module has provided me new insights into different topics; it has given me a chance to have a glimpse of others’ thoughts; it has enhanced my digital literacy rate.
Continue reading →








