Posts Tagged research
Competitors
There are few existing anonymous protesting networks at present, especially one site which combine anonymous and protest all together.
Protest.NET might be a good place to find where those upcoming protest event about to happen, however, it doesn’t provide discussion nor the security for some certain events. You can find out what when and where event is going to happen without struggle, easy but brings concerns for protesters in some other countries – local authorities do whatever it takes to prevent such thing happen.
Facebook and Twitter might be good place to call out for a protest, considering the large population base they have. But again, sensitive materials would be removed or banned at very beginning. So they won’t be the first choice either.
WHYWEPROTEST is quite a mature protest network, but only focusing on protesting Scientology. They do have forums to discuss other events take place internationally, but users are confused at the very beginning from entering the site, which looks more like a designed Scientology protesting site rather than to wider topics. Also the anonymity of the site is very weak – email address is required when registers and no compulsory to use secure/anonymous connection.
NoSQL
Posted by drakopoulos in Technical Details on May 1, 2012
NoSQL, which most now take to mean “Not Only SQL,” is a new non-relational approach to data management that supports dynamic and flexible schemas, optimized storage for web scale, and extreme performance as well as makes semi-structured and unstructured data easier to use and access. Although RDBMS technology is still a good fit for critical transactional applications, new types of applications are motivating architects to look elsewhere when the relational approach falls short. Craigslist, Facebook, Twitter, Yahoo, and YouTube have already used NoSQL to support demanding web-scale applications. Although adoption of NoSQL in enterprises is around 4%, Forrester expects this to double in the next two years and that by 2015, 20% of enterprises will use NoSQL to support some or all of their applications. This is one of the major reasons for choosing to use NoSQL.
NoSQL offers several benefits in the areas of data management, access, storage, scale, and performance that make it a viable alternative to RDBMS. NoSQL delivers:
Flexible schema structures to support new types of applications.
Unlike an RDBMS, which requires the application developer to predefine data attributes, entities, and relationships, NoSQL offers a more flexible approach in which the application rather than the data store defines the schema and access paths. NoSQL supports a wide range of new data types, including textual types such as JSON as well as many other unstructured and semistructured data types. NoSQL’s inclusion of these flexible schemas and data types makes it easier to build new types of social media, cloud, and other scale-out applications.
High-performance key-value data reads and writes.
Applications that require extensive data reads and writes often experience excessive latency due to disk input/output (I/O) bottlenecks, especially when the app has high volumes of both. NoSQL approaches are efficient at reading very large amounts of data in a scale-out model, with each node in a cluster having its own I/O channels and controllers to deliver linear scale. For example, Twitter spreads accounts across thousands of nodes using a key-value store, and millions of users get low latency while concurrently accessing data. Conversely, NoSQL is not well suited to joining entities unless the store contains prejoined data.
Elastic scale to support dynamic workloads.
Because of the need to partition data across multiple databases, it’s challenging to scale out an RDBMS to handle growth. This makes it challenging to use an RDBMS when building an application that can easily scale from a thousand to a million users. NoSQL’s shared-nothing, scale-out architecture makes it easy to add nodes in a cluster or cloud to deliver linear scale.
High-performance key-value data reads and writes.
Applications that require extensive data reads and writes often experience excessive latency due to disk input/output (I/O) bottlenecks, especially when the app has high volumes of both. NoSQL approaches are efficient at reading very large amounts of data in a scale-out model, with each node in a cluster having its own I/O channels and controllers to deliver linear scale. For example, Twitter spreads accounts across thousands of nodes using a key-value store, and millions of users get low latency while concurrently accessing data. Conversely, NoSQL is not well suited to joining entities unless the store contains prejoined data.
Elastic scale to support dynamic workloads.
Because of the need to partition data across multiple databases, it’s challenging to scale out an RDBMS to handle growth. This makes it challenging to use an RDBMS when building an application that can easily scale from a thousand to a million users. NoSQL’s shared-nothing, scale-out architecture makes it easy to add nodes in a cluster or cloud to deliver linear scale.
Freedom to innovate.
NoSQL is for application developers and programmers who want complete control and flexibility to store and access data in the manner they want without having to comply with the constraints and rigid structures an RDBMS imposes.
Five challenges of NoSQL
The promise of the NoSQL database has generated a lot of enthusiasm, but there are many obstacles to overcome before they can appeal to mainstream enterprises. Here are a few of the top challenges.
Maturity
RDBMS systems have been around for a long time. NoSQL advocates will argue that their advancing age is a sign of their obsolescence, but for most CIOs, the maturity of the RDBMS is reassuring. For the most part, RDBMS systems are stable and richly functional. In comparison, most NoSQL alternatives are in pre-production versions with many key features yet to be implemented. Living on the technological leading edge is an exciting prospect for many developers, but enterprises should approach it with extreme caution.
Support
Enterprises want the reassurance that if a key system fails, they will be able to get timely and competent support. All RDBMS vendors go to great lengths to provide a high level of enterprise support. In contrast, most NoSQL systems are open source projects, and although there are usually one or more firms offering support for each NoSQL database, these companies often are small start-ups without the global reach, support resources, or credibility of an Oracle, Microsoft, or IBM.
Analytics and business intelligence
NoSQL databases have evolved to meet the scaling demands of modern Web 2.0 applications. Consequently, most of their feature set is oriented toward the demands of these applications. However, data in an application has value to the business that goes beyond the insert-read-update-delete cycle of a typical Web application. Businesses mine information in corporate databases to improve their efficiency and competitiveness, and business intelligence (BI) is a key IT issue for all medium to large companies. NoSQL databases offer few facilities for ad-hoc query and analysis. Even a simple query requires significant programming expertise, and commonly used BI tools do not provide connectivity to NoSQL. Some relief is provided by the emergence of solutions such as HIVE or PIG, which can provide easier access to data held in Hadoop clusters and perhaps eventually, other NoSQL databases.
Administration
The design goals for NoSQL may be to provide a zero-admin solution, but the current reality falls well short of that goal. NoSQL today requires a lot of skill to install and a lot of effort to maintain.
Expertise
There are literally millions of developers throughout the world, and in every business segment, who are familiar with RDBMS concepts and programming. In contrast, almost every NoSQL developer is in a learning mode. This situation will address naturally over time, but for now, it’s far easier to find experienced RDBMS programmers or administrators than a NoSQL expert.
References
[1] Stonebraker, M. “SQL databases v. NoSQL databases.” Commun. ACM 53(4) (April 2010), pp. 10 – 11.
[2] Leavitt, N., “Will NoSQL Databases Live Up to Their Promise?,” Computer , 43(2), Feb. 2010 pp.12 – 14.
[3] Yuhanna, N., “NoSQL Offers New Options for Application Developers”, Forrester Research, September 2011, ID: 60237
[4] Hopkins, B., “Big Opportunities in Big Data”, Forrester Research, May 2011, ID: 59321
Omemo: an open source social storage platform
Posted by wang in Existing Similar Tools on April 30, 2012
What is Omemo
Omemo is a free and open source storage platform based on anonymous P2P communication system. It develops a special method which is everyone shares some parts of their hard drive to establish an enormous virtual hard drive throughout the world. It provides a possibility to set up a distributed storage network which might have limitless storage space. The most attractive feature of Omemo is, it’s totally anonymous, no matter users upload or download sources, all the data are transmitted through key-based routing and randomly assigning query source.
Omemo allows people to upload and organise files with anonymity and user can access their files from anywhere. No one can change or delete the files that users have shared in this social storage network and no one can trace or monitor the exchange of sources, just as a spokesperson said, “There is no way to know who uploads a file, nor who downloads it.” To some extent, it supports the spirit of freedom and democracy of the Internet.
Omemo is available for Windows platfrom only.
How does it work
Users should firstly share some space on their local hard drive and the programm will set up a virtual hard drive based on these shared space. The more users, the larger will this multimedia library be built.
Omemo uses a a ring-shaped DHT based on Chord, it can realise anonymous data transmission based on key-based routing and randomly assigned query source. The more detailed discusstion of Omemo technical information can be found in these two website:
1. OMEMO: einige technische Infos
2. OMEMO: anonymous drive sharing
Support & development
Unfortunately, Omemo has been defunct already. The latest released programme was still a beta version and it stopped the support of any upload/download actions.
Usage experience
As Omemo has stopped any supports of it’s operation, forum and wiki, I cannot run it by myself, but there is still several screenshots can be found in this review article:
Omemo Launches New P2P Network
References:
1. The World of Peer-to-Peer (P2P)
2. 5 Most Efficient Online Data Back Up And Bulk Storage Sites
3. Omemo Launches New P2P Network
4. Innovative P2P Network launched by Omemo
5. Omemo.com – Open Source Social File Storage
6. http://en.wikipedia.org/wiki/Omemo
Freenet: The Free Network
Posted by steiakakis in Existing Similar Tools on April 19, 2012
Freenet is free software which lets you anonymously share files, browse and publish “freesites” (web sites accessible only through Freenet) and chat on forums, without fear of censorship. Freenet is decentralised to make it less vulnerable to attack, and if used in “darknet” mode, where users only connect to their friends, is very difficult to detect.
Communications by Freenet nodes are encrypted and are routed through other nodes to make it extremely difficult to determine who is requesting the information and what its content is.
Users contribute to the network by giving bandwidth and a portion of their hard drive (called the “data store”) for storing files. Files are automatically kept or deleted depending on how popular they are, with the least popular being discarded to make way for newer or more popular content. Files are encrypted, so generally the user cannot easily discover what is in his datastore, and hopefully can’t be held accountable for it. Chat forums, websites, and search functionality, are all built on top of this distributed data store.
Freenet has been downloaded over 2 million times since the project started, and used for the distribution of censored information all over the world including countries such as China and the Middle East. Ideas and concepts pioneered in Freenet have had a significant impact in the academic world. Our 2000 paper “Freenet: A Distributed Anonymous Information Storage and Retrieval System” was the most cited computer science paper of 2000 according to Citeseer, and Freenet has also inspired papers in the worlds of law and philosophy. Ian Clarke, Freenet’s creator and project coordinator, was selected as one of the top 100 innovators of 2003 by MIT’s Technology Review magazine.
An important recent development, which very few other networks have, is the “darknet”: By only connecting to people they trust, users can greatly reduce their vulnerability, and yet still connect to a global network through their friends’ friends’ friends and so on. This enables people to use Freenet even in places where Freenet may be illegal, makes it very difficult for governments to block it, and does not rely on tunneling to the “free world”.
Freenet network:
The network consists of a number of nodes that pass messages among themselves. Typically, a host computer on the network runs the software that acts as a node, and it connects to other hosts running that same software to form a large distributed network of peer nodes. Some nodes are end user nodes, from which documents are requested and presented to human users. Other nodes serve only to route data. All nodes communicate with each other identically — there are no dedicated “clients” or “servers”. It is not possible for a node to rate another node except by its capacity to insert and fetch data associated with a key. This is unlike most other P2P networks where node administrators can employ a ratio system, where users have to share a certain amount of content before they can download.
Freenet may also be considered a small world network.
The Freenet protocol is intended to be used on a network of complex topology, such as the Internet (Internet Protocol). Each node knows only about some number of other nodes that it can reach directly (its conceptual “neighbors”), but any node can be a neighbor to any other; no hierarchy or other structure is intended. Each message is routed through the network by passing from neighbor to neighbor until it reaches its destination. As each node passes a message to a neighbor, it does not know or care whether the neighbor will forward the message to another node, or is the final destination or original source of the message. This is intended to protect the anonymity of users and publishers.
Each node maintains a data store containing documents associated with keys, and a routing table associating nodes with records of their performance in retrieving different keys.
This summary was written using the following sources:
[1] Freenet homepage
[2] Freenet papers
[3] Freenet wikipedia
The Onion Router (TOR)
Posted by taolu in Existing Similar Tools on April 18, 2012
 Tor is a system intended to enable on-line anonymity, originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Now tor has been used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
Tor is a system intended to enable on-line anonymity, originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Now tor has been used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
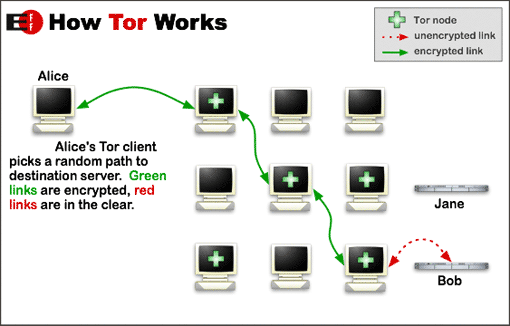
Tor helps to reduce the risks of both simple and sophisticated traffic analysis by distributing your transactions over several places on the Internet, so no single point can link you to your destination. The idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is tailing you — and then periodically erasing your footprints. Instead of taking a direct route from source to destination, data packets on the Tor network take a random pathway through several relays that cover your tracks so no observer at any single point can tell where the data came from or where it’s going.
To create a private network pathway with Tor, the user’s software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken. The client negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can’t trace these connections as they pass through. Once a circuit has been established, many kinds of data can be exchanged and several different sorts of software applications can be deployed over the Tor network. Because each relay sees no more than one hop in the circuit, neither an eavesdropper nor a compromised relay can use traffic analysis to link the connection’s source and destination. Tor only works for TCP streams and can be used by any application with SOCKS support. For efficiency, the Tor software uses the same circuit for connections that happen within the same ten minutes or so. Later requests are given a new circuit, to keep people from linking your earlier actions to the new ones.
Tor can’t solve all anonymity problems. It focuses only on protecting the transport of data. You need to use protocol-specific support software if you don’t want the sites you visit to see your identifying information. Tor does not provide protection against end-to-end timing attacks: If an attacker can watch the traffic coming out of your computer, and also the traffic arriving at your chosen destination, he can use statistical analysis to discover that they are part of the same circuit.
This summary was written using the following sources:
[1] Tor Homepage
[2] Wikipedia about Tor
[3] Tor wiki
Questionnaire
Posted by drakopoulos in Other on April 14, 2012
We came up with a set of questions revolving around our project and the issue we are dealing with, in order to gauge public opinion on the matter and gain further insight into who the potential users would be. This was not conducted as a survey, but rather as interviews with various individuals (university students and working professionals).
The following questions were asked:
1a. How would you characterize your usage of social networks?
1b. On a scale of 1 to 5 how active do you consider yourself on the social networks?
2. What social networks do you normally use and why?
3. What is your biggest concern regarding social network usage?
4. When signing up for a social network, do you read the Terms and Conditions? Why?
5. How important do you consider the right of freedom of speech?
6. Do you believe that same right to freedom of speech that exists in the physical world should also apply online?
7. What are your views of the current state of online freedom of speech and do you feel that it is being threatened?
8a. Have you ever refrained from posting something controversial (opinion/video/news article etc.) on the social networks?
8b. If so, why?
9. To what extent do think that your online activities on social networks are being monitored by the authorities?
10. Would you participate in a discussion online about a sensitive/controversial topic?
11. What are your views on censorship and do you believe that it is sometimes necessary? Please provide any relevant examples.
12. “You cannot guarantee freedom of speech and enforce copyright law.” Do you agree or disagree with this statement and why?
13. “You cannot have freedom of speech without the option to remain anonymous.” Do you agree or disagree with this statement and why?
14. If there was a social network that both allowed the users to remain anonymous and truly protect freedom of speech, would you participate and why?