Archive for category Existing Similar Tools
Omemo: an open source social storage platform
Posted by wang in Existing Similar Tools on April 30, 2012
What is Omemo
Omemo is a free and open source storage platform based on anonymous P2P communication system. It develops a special method which is everyone shares some parts of their hard drive to establish an enormous virtual hard drive throughout the world. It provides a possibility to set up a distributed storage network which might have limitless storage space. The most attractive feature of Omemo is, it’s totally anonymous, no matter users upload or download sources, all the data are transmitted through key-based routing and randomly assigning query source.
Omemo allows people to upload and organise files with anonymity and user can access their files from anywhere. No one can change or delete the files that users have shared in this social storage network and no one can trace or monitor the exchange of sources, just as a spokesperson said, “There is no way to know who uploads a file, nor who downloads it.” To some extent, it supports the spirit of freedom and democracy of the Internet.
Omemo is available for Windows platfrom only.
How does it work
Users should firstly share some space on their local hard drive and the programm will set up a virtual hard drive based on these shared space. The more users, the larger will this multimedia library be built.
Omemo uses a a ring-shaped DHT based on Chord, it can realise anonymous data transmission based on key-based routing and randomly assigned query source. The more detailed discusstion of Omemo technical information can be found in these two website:
1. OMEMO: einige technische Infos
2. OMEMO: anonymous drive sharing
Support & development
Unfortunately, Omemo has been defunct already. The latest released programme was still a beta version and it stopped the support of any upload/download actions.
Usage experience
As Omemo has stopped any supports of it’s operation, forum and wiki, I cannot run it by myself, but there is still several screenshots can be found in this review article:
Omemo Launches New P2P Network
References:
1. The World of Peer-to-Peer (P2P)
2. 5 Most Efficient Online Data Back Up And Bulk Storage Sites
3. Omemo Launches New P2P Network
4. Innovative P2P Network launched by Omemo
5. Omemo.com – Open Source Social File Storage
6. http://en.wikipedia.org/wiki/Omemo
Freenet: The Free Network
Posted by steiakakis in Existing Similar Tools on April 19, 2012
Freenet is free software which lets you anonymously share files, browse and publish “freesites” (web sites accessible only through Freenet) and chat on forums, without fear of censorship. Freenet is decentralised to make it less vulnerable to attack, and if used in “darknet” mode, where users only connect to their friends, is very difficult to detect.
Communications by Freenet nodes are encrypted and are routed through other nodes to make it extremely difficult to determine who is requesting the information and what its content is.
Users contribute to the network by giving bandwidth and a portion of their hard drive (called the “data store”) for storing files. Files are automatically kept or deleted depending on how popular they are, with the least popular being discarded to make way for newer or more popular content. Files are encrypted, so generally the user cannot easily discover what is in his datastore, and hopefully can’t be held accountable for it. Chat forums, websites, and search functionality, are all built on top of this distributed data store.
Freenet has been downloaded over 2 million times since the project started, and used for the distribution of censored information all over the world including countries such as China and the Middle East. Ideas and concepts pioneered in Freenet have had a significant impact in the academic world. Our 2000 paper “Freenet: A Distributed Anonymous Information Storage and Retrieval System” was the most cited computer science paper of 2000 according to Citeseer, and Freenet has also inspired papers in the worlds of law and philosophy. Ian Clarke, Freenet’s creator and project coordinator, was selected as one of the top 100 innovators of 2003 by MIT’s Technology Review magazine.
An important recent development, which very few other networks have, is the “darknet”: By only connecting to people they trust, users can greatly reduce their vulnerability, and yet still connect to a global network through their friends’ friends’ friends and so on. This enables people to use Freenet even in places where Freenet may be illegal, makes it very difficult for governments to block it, and does not rely on tunneling to the “free world”.
Freenet network:
The network consists of a number of nodes that pass messages among themselves. Typically, a host computer on the network runs the software that acts as a node, and it connects to other hosts running that same software to form a large distributed network of peer nodes. Some nodes are end user nodes, from which documents are requested and presented to human users. Other nodes serve only to route data. All nodes communicate with each other identically — there are no dedicated “clients” or “servers”. It is not possible for a node to rate another node except by its capacity to insert and fetch data associated with a key. This is unlike most other P2P networks where node administrators can employ a ratio system, where users have to share a certain amount of content before they can download.
Freenet may also be considered a small world network.
The Freenet protocol is intended to be used on a network of complex topology, such as the Internet (Internet Protocol). Each node knows only about some number of other nodes that it can reach directly (its conceptual “neighbors”), but any node can be a neighbor to any other; no hierarchy or other structure is intended. Each message is routed through the network by passing from neighbor to neighbor until it reaches its destination. As each node passes a message to a neighbor, it does not know or care whether the neighbor will forward the message to another node, or is the final destination or original source of the message. This is intended to protect the anonymity of users and publishers.
Each node maintains a data store containing documents associated with keys, and a routing table associating nodes with records of their performance in retrieving different keys.
This summary was written using the following sources:
[1] Freenet homepage
[2] Freenet papers
[3] Freenet wikipedia
The Onion Router (TOR)
Posted by taolu in Existing Similar Tools on April 18, 2012
 Tor is a system intended to enable on-line anonymity, originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Now tor has been used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
Tor is a system intended to enable on-line anonymity, originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Now tor has been used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
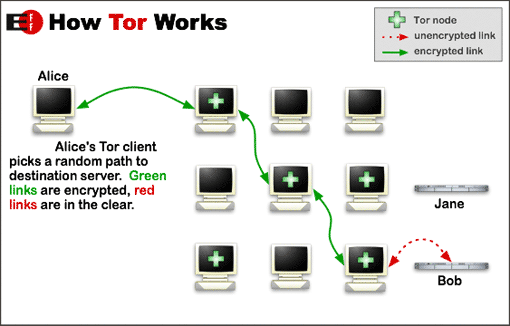
Tor helps to reduce the risks of both simple and sophisticated traffic analysis by distributing your transactions over several places on the Internet, so no single point can link you to your destination. The idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is tailing you — and then periodically erasing your footprints. Instead of taking a direct route from source to destination, data packets on the Tor network take a random pathway through several relays that cover your tracks so no observer at any single point can tell where the data came from or where it’s going.
To create a private network pathway with Tor, the user’s software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken. The client negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can’t trace these connections as they pass through. Once a circuit has been established, many kinds of data can be exchanged and several different sorts of software applications can be deployed over the Tor network. Because each relay sees no more than one hop in the circuit, neither an eavesdropper nor a compromised relay can use traffic analysis to link the connection’s source and destination. Tor only works for TCP streams and can be used by any application with SOCKS support. For efficiency, the Tor software uses the same circuit for connections that happen within the same ten minutes or so. Later requests are given a new circuit, to keep people from linking your earlier actions to the new ones.
Tor can’t solve all anonymity problems. It focuses only on protecting the transport of data. You need to use protocol-specific support software if you don’t want the sites you visit to see your identifying information. Tor does not provide protection against end-to-end timing attacks: If an attacker can watch the traffic coming out of your computer, and also the traffic arriving at your chosen destination, he can use statistical analysis to discover that they are part of the same circuit.
This summary was written using the following sources:
[1] Tor Homepage
[2] Wikipedia about Tor
[3] Tor wiki
Invisible Internet Project (I2P)
Posted by drakopoulos in Existing Similar Tools on April 17, 2012
I2P is an anonymizing network, offering a simple layer that identity sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties. I2P is designed to allow peers using I2P to communicate with each other anonymously – both sender and receiver are unidentifiable to each other as well as to 3rd parties. It can be used for anonymous: web surfing, chatting, blogging and file transfers.
The I2P network, a low-latency message oriented anonymous network was mainly designed to allow a fully anonymous conversation between two parties with the I2P network limits. The network itself is strictly message based (like IP), but there is a library available to allow reliable streaming communication on top of it (like TCP).
ALL communication is end-to-end encrypted (total of 4 layers of encyption) and even end-points are cryptographic identifiers (public keys) so that neither sender nor recipient of a message need to reveal their IP address to the other side (or to 3rd parties).
The network is formed of a group of routers. A router runs the software that allows any application to communicate through I2P. Applications running on top of it will have a destination associated, which receives incoming connections from third parties. The secret lies in which destination is associated to which router and not in the fact that a user is running an instance of the router. This uncoupling between the router and the destinations provides a certain degree of anonymity. The decentralized nature of the network prevents a single point of failure and adds another element of anonymity, as every client also acts as a server on the network.
The network itself is message oriented, in other words it is essentially a secure and anonymous IP layer, where messages are cryptographic keys (destinations) and can be significantly larger than IP packets. Furthermore, I2P has no official entry/exit points (in contrast to Tor), all peers participate in the mix, and there isn’t any network layer in or out proxies (however at the application layer, a few proxies exist).
How it works:
I2P uses bundled encryption over a multi-proxy like Tor. The packets are bounced all over the globe using I2P. However, the packets are encrypted with EIGamal and AES encryption. Using bundled encryption like this allows a packet to only decrypt the next hop as it passes through various nodes on its path. Once inside the network, IP addresses are not even used. Your node is assigned an address of garbled text to use an identifier.
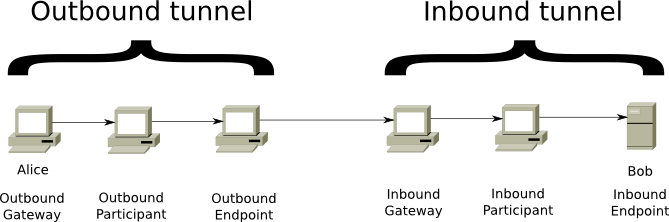
I2P uses virtual, unidirectional tunnels that pass through a series of routers, and are typically 2 to 3 hops. Each round trip message and reply will require 4 tunnels. One each for the sender and receiver’s inbound/outbound traffic. Tunnels are created using what is known as ‘garlic routing’. A tunnel build message is sent via garlic routing to an I2P router requesting that it participate in a tunnel.
I2P makes a strict separation between the software participating in the network (a ‘router’) and the anonymous endpoints (‘destinations’) associated with individual applications. The fact that somebody is running I2P isn’t usually a secret. What is hidden is the information on what the user is doing as well as what router a particular destination is connected to. End users will typically have several local destinations on their router.
This summary was written using the following sources:
[1] I2P Homepage
[2] I2P Tech Intro
[3] I2P Tunnel
[4] Getting Started On The I2P Darknet
[5] I2P – The *other* Anonymous Network