Archive for May, 2012
3speech on the World Wide Web
Posted by epan in Front-end Design, Other on May 10, 2012
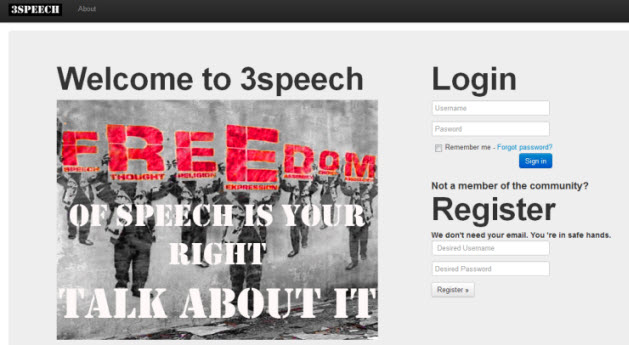
Since 3speech can only be accessed through the i2p network, we decided to raise awareness of our platform by using a domain in the World Wide Web. The figure below shows a screenshot of the created webpage.
The webpage will also contain details instructions on how to install i2p and reach the community of 3speech.
User Interface Screenshot
Posted by epan in Front-end Design on May 10, 2012
Based on the research on User Interface design and the choice of a navigation scheme, we started building a demo user interface.
First of all, we created the login page of 3speech. This is what we came up with:
The page will contain the following manifest:
From now on, it can never be the same as before…because the place we are from does not exist anymore.
The Web is changing, and not for the better. Online freedom of speech is under attack by authorities, corporations and governments. Lobbyists are twisting anti-piracy laws to hide their true intentions and to further their own agendas. Censorship is their weapon of choice and they are trying to utilize it to its fullest extent. They are trying to limit the free flow of information at the cost of your fundamental right to free speech. This cannot be accepted. This should not be accepted.
What we are seeing is only the beginning and things will only get worse. The only solution is to raise awareness and promote open conversations about the issues that matter. 3SPEECH is not the answer, but where the answers can be created.
It is the place where ideas and discussions can take place, allowing its users to remain unaccountable, untraceable and untouchable by current censorship methods.
Talk to your friends, talk to your family, talk to anyone that might be interested.
Competitors
There are few existing anonymous protesting networks at present, especially one site which combine anonymous and protest all together.
Protest.NET might be a good place to find where those upcoming protest event about to happen, however, it doesn’t provide discussion nor the security for some certain events. You can find out what when and where event is going to happen without struggle, easy but brings concerns for protesters in some other countries – local authorities do whatever it takes to prevent such thing happen.
Facebook and Twitter might be good place to call out for a protest, considering the large population base they have. But again, sensitive materials would be removed or banned at very beginning. So they won’t be the first choice either.
WHYWEPROTEST is quite a mature protest network, but only focusing on protesting Scientology. They do have forums to discuss other events take place internationally, but users are confused at the very beginning from entering the site, which looks more like a designed Scientology protesting site rather than to wider topics. Also the anonymity of the site is very weak – email address is required when registers and no compulsory to use secure/anonymous connection.
Scenarios and Personas 2
Posted by steiakakis in Scenarios and Personas on May 8, 2012
Scenarios and Personas 2:
Robert Nesta
Employer: Bank employee
Computer skills: Normal
Background Story
Robert Nesta is employed in a bank. He lives in Berlin and spends most of his free time on internet reading articles and news from around the world. He also is interested in discussing that news with other people. However, he is skeptical about the fact that he cannot risk revealing his identity. The majority of news websites require an account in order to allow the user to post a comment. Also he cannot express his thoughts on facebook, twitter or other social networks because he might be criticized by his company.
Scenario
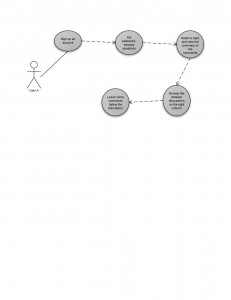
He has heard about 3speech. He needs to download the i2p network and install it on his computer. After he is done with the configurations and settings he is ready to browse 3speech. He logs in to his account and starts following discussions that are already held in 3speech. Also he is able to fetch an article or a media file from another website and start a discussion around it. Inside 3speech he has no identity; he is absolutely untraceable and free to express his ideas without any concern. Finally he is able to start building a discussion society around his interests and interact with other users.
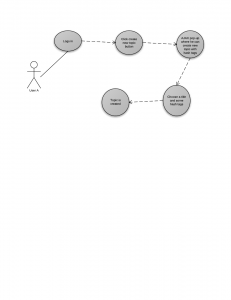
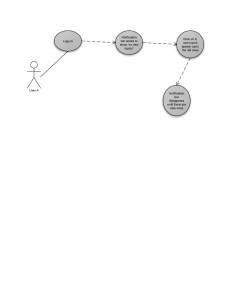
Use Case Diagrams
Posted by steiakakis in Scenarios and Personas on May 7, 2012
Functionalities and Requirements
Posted by steiakakis in Technical Details on May 6, 2012
Register
| # | Requirement | Description |
| 1 | Required fields | Username, Password, 3 Secret Questions, 3 Secret Answers |
| 2 | User Verification | Insert password twice.
Acceptance of Terms and Conditions. |
Login
| # | Requirement | Description |
| 3 | User Details | Username and password to gain access |
| 4 | Password Retrieval | A user can retrieve his password if he provide the correct answers to secret questions |
Edit Profile
| # | Requirement | Description |
| 5 | User Details | A user can edit his personal details providing all the required fields. |
Add Supporter
| # | Requirement | Description |
| 6 | View Supporters list | A user can add another user to his supporters list. |
Support Requests
| # | Requirement | Description |
| 7 | View Support requests list | A user can view his support request list. He can accept or reject a request from another user. |
View Supports list
| # | Requirement | Description |
| 8 | View Supports list | A user can view his supports list which contains all the users that he supports. |
Sent Message
| # | Requirement | Description |
| 9 | Create new message | A user can send a personal message to another user. The receiver can accept or decline this message. If he accepts the communication from a user, that user is inserted on his trust list. |
Add to trust list
| # | Requirement | Description |
| 10 | Add a user to support list | A user can view his trust list that contains the users that he trusts to communicate with. |
Add to block list
| # | Requirement | Description |
| 11 | Add a user to block list | A user can view his block list that contains the users that he does not want to receive messages from. |
Search
| # | Requirement | Description |
| 12 | Search for a topic | A user can search for his desired topic using hashtags. |
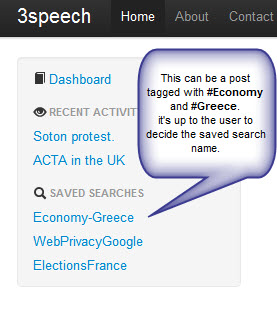
Save Search
| # | Requirement | Description |
| 13 | Save a specific search | A user can save his favourites search gaining easier navigation. |
Upload Picture
| # | Requirement | Description |
| 14 | Upload a profile picture | A user can upload a picture and store it in his profile. He can also delete that picture. |
Create new topic
| # | Requirement | Description |
| 15 | Create new topic | A user can create a new topic of his interest using the provided form. The topic needs a title and some hashtags in order to be categorized. |
Comment a topic
| # | Requirement | Description |
| 16 | Comment on a topic | A user can create a new comment under a topic or another comment. |
Scenarios and Personas 1
Posted by steiakakis in Scenarios and Personas on May 4, 2012
Alaa Abdel-Fattah : “Arrested by Egyptian Junta ”
Employer: Blogger
Background: Famous blogger
Computer skills: Advanced
Background Story
Alaa Abdel-Fattah , one of Egypt’s most famous bloggers and activists , was arrested in 2006 during a peaceful protest. Someone can state that this was a random arrest of a protestor. Six years later, it is common known that he had been arrested because of his blog’s significant reputation. It was another example of the systematic targeting of journalists, bloggers, and activists by Supreme Council of the Armed Forces (SCAF). This is a real example of internet free speech criminalization. Abdel-Fattah was not the only person that had been arrested for expressing freely his ideas. Many people around the globe had been banned from social networks and other websites for expressing their thoughts.
Scenario
Abdel-Fattah wants to continue blogging and posting his ideas and thoughts. But he is concerned about his own safety and freedom. With 3speech available he is now able to spread his thoughts without any hesitation.
He has heard about 3speech. He needs to download the i2p network and install it on his computer. After he is done with the configurations and settings he is ready to browse 3speech. He logs in to his account and starts following discussions that are already held in 3speech. Now he is able to view any topic of his interest, comment it or start his own new topic about the subject of his interest.
Hosting on I2P
Posted by drakopoulos in Technical Details on May 3, 2012
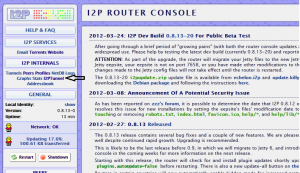
The default install of I2P comes with a Jetty web daemom, so starting up the eepsite is actually incredible easy. On the router console homepage, in the left hand bar there is a link to the I2PTunnel under the heading I2P Internals.
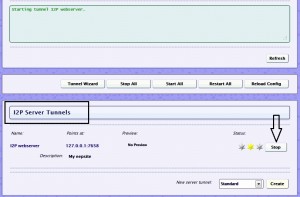
Once inside, in the I2P Server Tunnels section, you will see the default eepsite. Click the start button, and wait for it to start up.
On Windows, at this location: C:\Program Files\i2p\eepsite is where you will find the index.html file of the eepsite. There are some redirect to help instructions in the file, once those are deleted things are good to go.
Of course, the destination of the eepsite is on the local host and it will be difficult for other people to find because it doesn’t have a name and they don’t have your really long Base64 key. You could just tell people that really long key, but thankfully I2P has an address book and several easy ways to tell people about your eepsite.
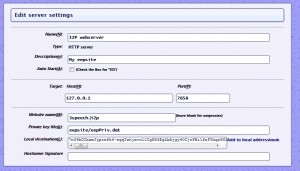
First, enter the new name of the eepsite on the eepsite i2ptunnel configuration page where it says “Website name”. This will replace the default “mysite.i2p”.
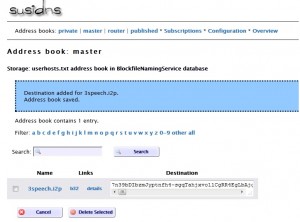
Highlight the entire “Local destination” key on the eepsite i2ptunnel configuration page and copy it for later pasting. Make sure you get the whole thing – it’s over 500 characters and it must end in “AAAA”. Enter the name and paste in the destination key into your master address book. Click “Add” to add the destination to your address book.
The final step is registering the eepsite in an address book hosted by i2p, which is part of the NetDB (explained in the about I2P post). Go to stats.i2p. Again, your key is the entire “Local destination” key on the eepsite i2ptunnel configuration page. After adding it, we can check to see if it reports the key was added. Since many routers periodically get address book updates from these sites, within several hours others will be able to find your website by simply typing 3speech.i2p into their browser.
We also used this video to learn how to host an eepsite by creating a new HTTP server tunnel and to map it to a virtual host rather than use the default Jetty. We did not actually do this because we do not have an external server to use.
Technologies Used
Posted by drakopoulos in Technical Details on May 2, 2012
Programming Language / Framework
The chosen language of 3speech implementation is Ruby, which is a dynamic, reflective, general-purpose, open source, object-oriented programming language. Ruby supports multiple programming paradigms, including functional, object oriented, imperative and reflective. 3speech was developed using the Ruby on Rails, open source full-stack web application framework which is a variant of the Model/View/Controller (MVC) architecture pattern to organize application programming. Ruby on Rails is a full-stack framework, meaning that it gave us the full ability to gather information from the web server, talking to or querying the database, and template rendering out of the box.
Web Server
I2P Webserver – A tunnel pointed to a Jetty webserver run on localhost:7658 for convenient and quick hosting on I2P.
The document root is:
Unix – %APPDATA%\I2P\eepsite\docroot
Windows – C:\Users\**username**\AppData\Roaming\I2P\eepsite\docroot
A future consideration is to use server virtualization, which is the partitioning of a physical server into smaller virtual servers to help maximize our server resources. In server virtualization the resources of the server itself are hidden, or masked, from users, and software is used to divide the physical server into multiple virtual environments.
Server virtualization also conserves space through consolidation as several machines can be consolidated into one server running multiple virtual environments. It also utilizes resources to the fullest so we can also save on operational costs (e.g. using a lower number of physical servers reduces hardware maintenance).
Database choice: NOSQL
NoSQL, which most now take to mean “Not Only SQL,” is a new non-relational approach to data
management that supports dynamic and flexible schemas, optimized storage for web scale, and
extreme performance as well as makes semi-structured and unstructured data easier to use and
access. Although RDBMS technology is still a good fit for critical transactional applications, new types of applications are motivating architects to look elsewhere when the relational approach falls short. Craigslist, Facebook, Twitter, Yahoo, and YouTube have already used NoSQL to support demanding web-scale applications. Although adoption of NoSQL in enterprises is around 4%, Forrester expects this to double in the next two years and that by 2015, 20% of enterprises will use NoSQL to support some or all of their applications. This is one of the major reasons for choosing to use NoSQL.
NoSQL offers several benefits in the areas of data management, access, storage, scale, and performance that make it a viable alternative to RDBMS. NoSQL delivers:
Flexible schema structures to support new types of applications.
Unlike an RDBMS, which requires the application developer to predefine data attributes, entities, and relationships, NoSQL offers a more flexible approach in which the application rather than the data store defines the schema and access paths. NoSQL supports a wide range of new data types, including textual types such as JSON as well as many other unstructured and semistructured data types. NoSQL’s inclusion of these flexible schemas and data types makes it easier to build new types of social media, cloud, and other scale-out applications.
High-performance key-value data reads and writes.
Applications that require extensive data reads and writes often experience excessive latency due to disk input/output (I/O) bottlenecks, especially when the app has high volumes of both. NoSQL approaches are efficient at reading very large amounts of data in a scale-out model, with each node in a cluster having its own I/O channels and controllers to deliver linear scale. For example, Twitter spreads accounts across thousands of nodes using a key-value store, and millions of users get low latency while concurrently accessing data. Conversely, NoSQL is not well suited to joining entities unless the store contains prejoined data.
Elastic scale to support dynamic workloads.
Because of the need to partition data across multiple databases, it’s challenging to scale out an RDBMS to handle growth. This makes it challenging to use an RDBMS when building an application that can easily scale from a thousand to a million users. NoSQL’s shared-nothing, scale-out architecture makes it easy to add nodes in a cluster or cloud to deliver linear scale.
Simplicity that makes it easy to get started.
NoSQL solutions have a fourth of the features of a typical RDBMS. This makes NoSQL easier to learn than a traditional DBMS as well as simpler to use when developing and deploying applications. From what we heard in interviews in the past year, many application developers like the simplicity and ease of using NoSQL in development. When using NoSQL, application developers have complete control over data storage and access and typically don’t need a database administrator (DBA) to support the NoSQL data store.
A lower-cost data management platform.
Many NoSQL solutions are open source, and others sell for much less than a full version of a commercial RDBMS. Compared with conventional DBMSes, NoSQL products often save enterprises more than 50% of the cost.
Freedom to innovate.
NoSQL is for application developers and programmers who want complete control and flexibility to store and access data in the manner they want without having to comply with the constraints and rigid structures an RDBMS imposes.
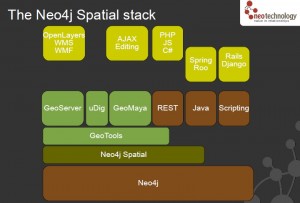
Neo4j is an open-source graph database, implemented in Java. The developers describe Neo4j as “embedded, disk-based, fully transactional Java persistence engine that stores data structured in graphs rather than in tables”.
Key benefits*
A graph data model which enables high performance queries on the complex, connected data inherent in today’s applications. You can ask questions such as “Who are all my contacts in Europe?” and “Which of my contacts ordered from this catalog?” It can traverse complex graphs with improvements of 1000x or more compared to SQL and other NOSQL databases.
A graph data model which simplifies the development of applications using complex, connected data. Enterprises can quickly capture all kinds of data – structured, semi-structured, and unstructured – and easily store it in Neo4j. This results in shorter development times, lower maintenance costs and higher performance.
Mature support for transactions so that enterprise developers can execute “all or nothing” transactions. Although this is a must-have for relational databases, none of the other NOSQL databases can do this. Neo4j supports full ACID transactions including XA-compliant distributed two-phase commits.
Enterprise-grade durability that ensures that any transaction committed to the database will not be lost. I
Awesome Java support. While supporting all of the leading development platforms, (Ruby, Python, Groovy, Gremlin, etc) Neo4j began in Java and will always be easily accessible and available for Java, the most widely used development environment in the enterprise.
This was also incredibly help full in helping us learn about representing our social network in the database: Social Network in the Database: Using a Graph Database
*Taken from the neo4j website.