I2P is an anonymizing network, offering a simple layer that identity sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties. I2P is designed to allow peers using I2P to communicate with each other anonymously – both sender and receiver are unidentifiable to each other as well as to 3rd parties. It can be used for anonymous: web surfing, chatting, blogging and file transfers.
The I2P network, a low-latency message oriented anonymous network was mainly designed to allow a fully anonymous conversation between two parties with the I2P network limits. The network itself is strictly message based (like IP), but there is a library available to allow reliable streaming communication on top of it (like TCP).
ALL communication is end-to-end encrypted (total of 4 layers of encyption) and even end-points are cryptographic identifiers (public keys) so that neither sender nor recipient of a message need to reveal their IP address to the other side (or to 3rd parties).
The network is formed of a group of routers. A router runs the software that allows any application to communicate through I2P. Applications running on top of it will have a destination associated, which receives incoming connections from third parties. The secret lies in which destination is associated to which router and not in the fact that a user is running an instance of the router. This uncoupling between the router and the destinations provides a certain degree of anonymity. The decentralized nature of the network prevents a single point of failure and adds another element of anonymity, as every client also acts as a server on the network.
The network itself is message oriented, in other words it is essentially a secure and anonymous IP layer, where messages are cryptographic keys (destinations) and can be significantly larger than IP packets. Furthermore, I2P has no official entry/exit points (in contrast to Tor), all peers participate in the mix, and there isn’t any network layer in or out proxies (however at the application layer, a few proxies exist).
How it works:
I2P uses bundled encryption over a multi-proxy like Tor. The packets are bounced all over the globe using I2P. However, the packets are encrypted with EIGamal and AES encryption. Using bundled encryption like this allows a packet to only decrypt the next hop as it passes through various nodes on its path. Once inside the network, IP addresses are not even used. Your node is assigned an address of garbled text to use an identifier.
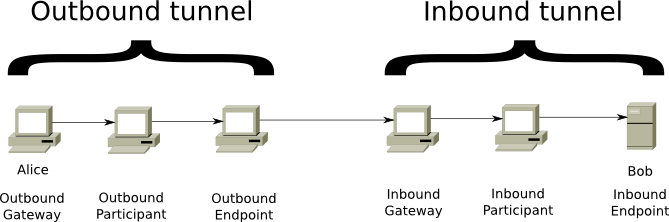
I2P uses virtual, unidirectional tunnels that pass through a series of routers, and are typically 2 to 3 hops. Each round trip message and reply will require 4 tunnels. One each for the sender and receiver’s inbound/outbound traffic. Tunnels are created using what is known as ‘garlic routing’. A tunnel build message is sent via garlic routing to an I2P router requesting that it participate in a tunnel.
I2P makes a strict separation between the software participating in the network (a ‘router’) and the anonymous endpoints (‘destinations’) associated with individual applications. The fact that somebody is running I2P isn’t usually a secret. What is hidden is the information on what the user is doing as well as what router a particular destination is connected to. End users will typically have several local destinations on their router.
This summary was written using the following sources:
[1] I2P Homepage
[2] I2P Tech Intro
[3] I2P Tunnel
[4] Getting Started On The I2P Darknet
[5] I2P – The *other* Anonymous Network