Archive for the ‘Uncategorized’ Category
Effects of the physical and environmental factors on the perception of privacy on the web amongst teenagers no comments
I am very interested to investigate the potential effects of the physical and environmental factors on the perception of privacy on the web amongst teenagers.
Environmental factors (such as the room that we publish our information from) or physical factors (such as the medium or device that we use and it’s characteristics including its size or portability) can play a crucial role in our perception of privacy. Examples of this can be seen amongst teenagers.
I found myself very interested in this subject after reading an article by Elizabeth Kandel Englander on cyberbullying that was published on the Harvard Education Letter recently. As part of this article Englander talks about the effects of the physical environment (including the location or size of the screen) on the perception of privacy amongst teenagers. She writes:
“In a study I’m currently conducting, about half of the teens who said they had sent or posted something they regretted said they did so while in their bedrooms—and 83 percent said it happened from a room inside their home. About two-thirds said they were using a device with a small screen—which can also promote a false feeling of privacy, since the screen size means that others can’t easily read over your shoulder. ”
But what exactly triggers this ? How does our brain trick us into believing that what we are sharing online is not going to be seen by many people and how do we get persuaded ? What is the thought process from the moment that our sensors collect information about the environment until the moment that the perception happens ? What role does biology play in creating the illusion of privacy in our brains?
I would like to approach this subject from the perspectives of cognitive psychology and cognitive neuroscience.
cognitive psychology:
I believe that approaching ideas about perceptions of privacy through perceptual psychology as a subset of cognitive psychology could shed light on how the teenage mind could interpret the stimuli from the physical environment in a way that it could create an illusion of privacy. Cognitive psychology could also help determine the cognitive processes that occur within the minds of the said teenagers which could direct the physical senses to lead into such conclusions.
cognitive neuroscience:
Despite it being a very fast-growing field, neuroscience still has many questions unanswered. As it is a very diverse and wide discipline, I’m planning to focus on very basic details of the cognitive levels. This is perhaps an intersection between neuropsychology and biology and could potentially be where an expert cognitive-neuroscientist could come up with answers to complex questions about the way that the brain interacts with the environment. Without looking for answers, this could be a great opportunity to try to look at the issue from the perspective of a neuroscientist.
Some textbooks that I’m planning to use:
- Cognitive Neuroscience: The Biology of the Mind , Michael Gazzaniga , Richard B. Ivry , George R. Mangun
- The Student’s Guide to Cognitive Neuroscience, Jamie Ward
- Cognitive Psychology and its Implications, John R. Anderson
- Cognitive Psychology , Robert L. Solso, Otto H. MacLin, M. Kimberly MacLin
‘Pornwall’: Digitally blindfolding web access to Pornography in the UK through automatic filtering to help protect young people. no comments
It goes without saying that pornography is open for academic debate from a significant number of different stances. Psychology, Sociology, Gender Rights, Politics, Equality, Misogyny, Criminology. The list goes on, the standpoints go even further. The impact of its usage has been debated extensively, sometimes without a clear conclusion. It raises interesting notions: does access to hardcore adult material promote inappropriate expectations in relationships? Is it degrading? Should service providers, such as Netflix and Microsoft, be allowed to provide streaming access to such sites through their dashboard? What does the scope and span of different types and forms say about our society as a whole? How do we define sexual content on the web and what percentage of its totality does it occupy?
The last notion intrigued me sufficiently to look it up. The main direction of reference denotes Phillip Stark’s 2006 study at the University of Berkley into the matter as a cited point of consideration. The findings suggested that 1.1% of the entire web was made up of pornography, based on an analysis of index referencing by Google and Microsoft. Of course, the web was a very different place 7 years ago. If you were to believe Avenue Q, feel free to conduct your own enquiry into their songs on the matter through Youtube, its all the web is used for these days. A more recent study, outlined by Forbes when the .XXX domain launched in 2011, by Ogas and Gaddam two researchers on the topic, asserted that in 2010 4% of the most popular (those most trafficked) websites were sexually themed. Further to this, from July 2009 to July 2010, approximately 13% of web searches were for erotic content. [Ogas et.al, 2011, stated in Forbes: ‘How much of the Internet is actually for Porn?’, http://www.forbes.com/sites/julieruvolo/2011/09/07/how-much-of-the-internet-is-actually-for-porn/].
The article raised some interesting further notions that I might come back and consider, but most notably it raised a link to my focus topic: the current decision by the government to create what could be affectionally termed a ‘pornwall’, a united approach by the UK ISP industry to automatically filter out materials of an adult nature and content. The justification for this was a morally sound one- to prevent young people, in particular young children, from accessing pornographic material or adult content either through deliberate effort, or unintentional consequence. It is an easy scenario to envisage where a child, studying tourism as part of their Geography curriculum programme of study which is covered in both the Primary and Secondary programmes of study, investigates Amsterdam because they really like the paintings of Van Gogh and finds instead a range of adult material.
The concept has intrigued me since David Cameron spoke in July 2013 on Radio 2, answering questions from a variety of irate callers who objected to both loss of freedom and practicality of the proposal. Especially as it was to be applied to all new broadband subscribers, not those pre-existing. His outline at this point was almost entirely pornographically focused, as he had yet to assert the broader implications of filtering other topics, such as anorexia, terrorism and esoteric material. These three could be open to debate- there is a plausible argument that these topics shouldn’t be automatically filtered, especially if some are educative. After all, the Bible is esoteric. [http://www.huffingtonpost.com/2013/07/29/uk-internet-filter-block-more-than-porn_n_3670771.html]
It also prompted the first of my two discipline enquiries, albeit in a round about way- the technical Computer Science of the web. I was left thinking could such ‘debatable’ topics be automatically filtered or are they distinguishable? How in fact do such filters work? Actually what is a filter? In fact, come to mention it, how does searching for websites actually work? Would the entire web collapse if we start hacking out parts of it and preventing people from gaining access instantly? Would this be user-focused or ISP focused? A point strongly argued in defence of this ‘pornwall’ was that it helped to reduce illegal pornography. However, can such filters actually detect downloads through file sharing services or peer to peer networks? I don’t have any understanding beyond the basis that such services exist- but I’d wager probably not if you change the file name?
The difference on that last question, I feel, is quite important. I’ve known my fathers password to the computer since I was old enough to use a computer. Having about as much knowledge of computers as I do aerodynamics or quantum theory, it didn’t take a genius to click on the password hint button on the windows log in page, which promptly asked me ‘What is your mothers name?’. Fairly certain I knew that. If it were to be this simple today, what would be the point? It goes without saying that the average young person these days is probably a little bit quicker off the mark than I was on Windows 95. Especially, as noted by Ofcom, there still exists an existing situation where 60% of parents don’t have any of their own user-based filters in place. [Hawkes, 2013, citing Ofcom 2013 study, noted in http://www.telegraph.co.uk/technology/internet/10354088/Nearly-60-per-cent-of-parents-have-no-filters-in-place-to-protect-their-kids-on-the-internet.html].
Having worked in an environment where I have seen, first hand, the severe impact it can have on young people my stance on it has always been split between professional attitude and personal freedoms. In fact, such reasoning led me to a point that wasn’t focused upon in the interview; it argued any step that protects young people, no matter how realistically applicable, is worthwhile. I agree, in principle, but first hand experience in dealing with such an issue made me associate this notion to a blindfold. To elaborate if 100% of filters were in place, consistently, with no breaks in the chain, a universal ‘pornwall’ would create a ‘digital blindfold’ that meant no young people would ever access adult material unintentionally. The problem with such a metaphor is that such a blindfold could slipped off relatively easily, just like in real life, especially if there was a notion of intention on the young persons part and shared just as easily without using a home computer. To an extent, this balance of debate linked to my second field of study, Philosophy and Ethics. This in itself raises a number of questions I hope to explore in relation to the topic, such as moral responsibility, ethics of decision making in politics as well as personal freedoms, entitlements and rights. Whilst Philosophy might have been better paired with a subject such as Psychology on this topic, I’m intrigued as to the ways in which the two can be inter-related. Can parallels be drawn?
A stance I’ve recently considered in this regard is whether it is right to make such a decision on behalf of the society, then as an individual have a consequential result of being monitored opting-out. Will this paint you more likely as a potential sexual deviant? Can it be monitored? Should it? Both disciplines could, feasibly, lend considerations to each other in this regard and possibly others.
The Digital Afterlife – What happens to our data when we die? no comments
As an undergraduate, I wrote my dissertation on the surrender of secrecy on social networking sites with a focus on Facebook, Twitter and Instagram. Through studying two age cohorts I discovered that young people, so called ‘digital natives’, often used their respective social networking profiles as a means to both establish and experiment with their emerging identities in different ways. On the other hand, older participants, aged between 45 and 50, took a very functional approach to social networking online.
Throughout my study all participants talked of uploading information like family photos, home movies and personal messages and achievements. However, not one participant talked about the future of their online profiles – no one seemed to realise, or be concerned by, the fact that they were moving their future heirlooms into more or less solely digital form through services like Facebook, YouTube and Gmail.
A rich chronicle of life is being created online and therefore I am interested in digital death and legacy. Do we have the right to be forgotten? Who now owns our memories? As, for the first time, users begin to pass away, who should have control over the data they leave behind, especially data that is so sentimental and personal?
So, I choose to look at this topic through the eyes of Law and Anthropology.
Law
Law, I believe, can provide insight into the rights of users and be progressive in determining new legislation for the future.
(Really I know nothing about Law so I hope to be more articulate with this soon…)
Anthropology
I’m anticipating an Anthropological approach to be entirely different to Law – I have briefly studied a little Anthropology in the past and believe that it’s field-based, subjective approach could provide some useful insight to how users might feel about the real and digital deaths of those they love. Similarly, they have their own digital death to consider… Should physical and digital death be synonymous?
To conclude, I hope to bright together a discipline I consider to be objective, Law (please correct me if I’m wrong!), with one that appears entirely subjective, Anthropology.
A starting point 1 comment
The question I hope to approach (unless I get that “Are you sure?” email from Les) is “How can we design a better user interface?”. In case you’re not sure of the terminology, I take “user interface” to mean any way in which people interact with a computer, from graphical user interfaces (GUIs) to physical hardware like mice and touchscreens, text-to-speech for visually impaired people, and even gesture based interfaces like Kinect and LeapMotion.
I like this as a topic because for 95% of computer scientists and programmers (like me) in the real world it’s not even a consideration; of course the website will be good, just look how well the server processes data. After all, what’s the point of building something great if only people with a computing degree can understand what the obscure symbols on the tiny buttons are supposed do?
The two subject areas I chose to analyse my question are Geography and Biology. They may seem obscure for this kind of problem, but they’re not totally off the wall, and here’s why:
Biology, the study of life
The systems we design are for people, so the study of people has a lot to offer this problem. It could be from a purely physical standpoint looking at the size and shape of people (Biological Anthropology), like whether they can actually reach the top of a touchscreen (thanks Galaxy Note, you don’t really work here). It could also be the application of biological principles like natural selection to interface designs; if I get 1000 people to trial several designs then we take the best ones forward to the second round of testing.
Geography, the study of the world around us
This one’s a bit more obscure and possibly harder to apply, however geography has some of the oldest methods of representing and simplifying data to make it more accessible to people. Cartography (Physical Geography) has been making it possible for people to get around for hundreds of years, and the census (Human Geography) takes information about the entire population and presents it in easy to read statistics.
Hopefully there’s a lot of potential for both of these and over the next few weeks I’ll be digging further to find out exactly what can be applied and how. If anyone has any thoughts then please add a comment or come over and find me.
Managing strategy no comments
Having promised a blog post on management’s perspective of global issues, I still haven’t found the right articles to help me. Unable to clearly articulate how management as a discipline would approach a global issue, I thought it was mainly because management deals with organisations – therefore actors in its ontology are well defined and my issue of the global digital divide to a certain extent involves the non-existence of organisations, and a system that transcends other organisations. Having done a bit more thinking I now believe that management as a discipline would not directly tackle the issue of the global digital divide, but focus on the actors who were actively involved in trying to achieve something to do with the global digital divide.
This is where the idea of strategy comes into play. And to find more information on that I looked at chapter 8 in Boddy’s introduction to management.
Boddy defines strategic management as that which ‘enables companies to be clear about how they will add value to resources, even though much is changing in their world. Strategy links the organisation to the outside world, where changes in the competitive (micro) and wider (macro) environments bring opportunities and threats.’ There are two main aspects of strategy – its process and its content, and both exist in a context. Boddy states that ‘whatever their context, strategists hope that their work will enhance performance by clarifying and unifying purpose, reducing uncertainty, linking short-term actions to long-term goals and providing control – since setting goals provides standards again which to measure performance’.
There are three perspectives on the strategy process – planning, learning and political. The planning view involves a formal process based on a vast amount of information. It is based on the assumptions that events and facts can be observed objectively and that people respond rationally to information.
The learning view sees strategy as an emergent or adaptive process, more suited for businesses in rapidly changing sectors or environments which require a more flexible approach.
In the political view, the notion of power, conflict and ambiguity are introduced, where strategic management is ‘not a scientific, comprehensive or rational process, but an iterative, incremental process, characterised by restricted analysis and bargaining between the players’.
After finding various organisations that actually work on addressing the global digital divide, I believe I will be able to provide a sound discussion on how the discipline of management would approach such a topic, the results of which will be found in my report in January 2013.
References
Boddy D. (2010) Management: An Introduction, 5th edition, Harlow: Financial Times Prentice Hall
Management Models no comments
Last week I wrote about an introduction to the basic concepts and perspectives in the discipline of management promising a review of some management models this week. This is a summary of Boddy’s second chapter ‘Models of Management’.
Boddy defines a model as aiming to ‘identify the main variables in a situation, and the relationships between them: the more accurately they do so, the more accurate they are.’ A model furthermore provides a ‘mental toolkit to deal consciously with a situation’. Boddy emphasise that managers can draw upon different models according to the varied situations they face – what is important is understanding the values embodied in the model or theory and act accordingly. That is also known as thinking critically about a situation, an essential skill in management.
Boddy and others identify four key types of models of management according to their underlying philosophies:
- rational goal
- internal process
- human relations
- open systems
Rational goal models
Some of the first kinds of models to have been developed, their origins are found in the formation of the modern firm, during the Industrial Revolution, where managers were face with the need to manage new organisational structure profitably. It evolved from the tradition of scientific management and operational research. The model emphasise the aim of maximising output/profit through enhanced control and quantitative information as a basis for decision-making.
Internal process models
These come from the Weberian bureaucratic management ideas and from Henri Fayol’s notion of ‘administrative management’ which emphasise rules and regulations over personal preferences, division of labour and hierarchical structure. While the concept of bureaucracy has been widely criticised (notably for stifling creativity) it has been supported when it allows employees to master their tasks therefore enhancing security and stability and is still widely used today, notably in the public sector.
Human relations models
These theories were developed when experiments on working conditions (lighting or other material factors) produced unexpected results. It was shown that altering the environment positively or negatively, output from the experimental team still increased. Elton Mayo, invited to comment on the results, asserted that output growth was the result of the new social relations established in the team. Individuals felt special, they were asked for their opinion, and as part of the experiment fully collaborated with one another. This led theorists to emphasise the importance of social processes at work, including the well-being of employees.
Open systems
Finally open systems models where the organisation is seen ‘not as a system but as an open system’, which interacts with its environment. Resources are imported, undergo transformations and turned into output that generate profit. Information about the performance of the system goes back as a feedback loop into the inputs. Important variants include socio-technical systems where outcome depends on the interaction of technical and social subsystems. Another is the notion of contingency management which emphasises the need for adaptability to the external environment. And finally complexity theory which focuses on the complex systems, their dynamics and feedback loops where agents within the system interact autonomously through emergent rules. These emphasise the non-linearity of change in organisations.
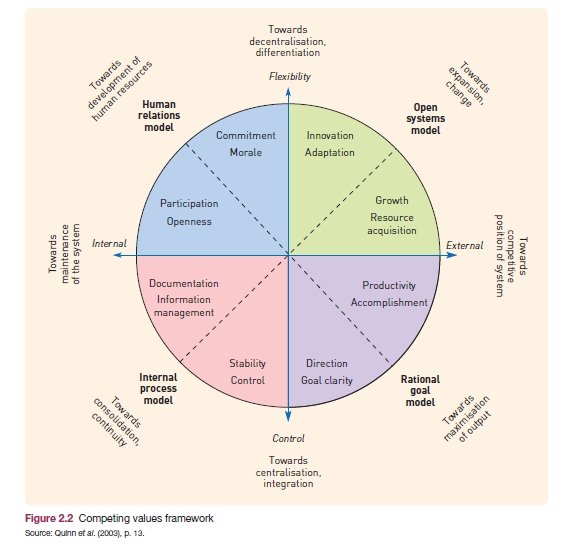
The table below provides a summary of the four models (from Boddy 2010, p. 61).
In fact management theorists Quinn et. al. (2003) believe that the four successive models of managements complement rather than contradict each other, and they provide a framework that integrates these various model – the ‘competing values framework
Next week I will look to read about management and global issues to get a better grasp of the discipline’s approach to an issue that transcends its main ontological actor – the organisation.
References
Boddy D. (2010) Management: An Introduction, 5th edition, Harlow: Financial Times Prentice Hall
Quinn, R.E., Faerman, S.R., Thompson, M.P. amd McGrath, M.R. (2003) Becoming a Master Manager: A Competency Framework, 3rd ed., Hoboken: John Wiley & Sons
Free Open Internet? The Battle against SOPA, DMCA, ACTA and PIPA no comments
This week I have been researching around the current topic of political hacking movements regarding the, recently introduced, government legislation on the web. The political movements have been ‘clubbing together’ to battle the right to a free and open internet. This appears to be something that governmental bodies and political parties are worried about, but however does not seem to stop the hackers themselves crashing, changing or damaging government websites. Furthermore, it seems that word-of-mouth through social sites is something that is a huge battle for governmental bodies to win. If the voice of the ‘everyman’ were to get censored then this would indeed question the level of democracy in our country.
A recent film, found here, inspired me to review this topic in my interdisciplinary study, as it is a current topic that will effect all internet users across the world, and indeed leads me to question whether the grouping together of hackers and hacktivists worldwide will make any difference in the political and legal legislation that has been put forward. I will be following this film over the next few months and hopefully will be able to view the finished film early next year.
I have found it reasonably difficult to find books regarding the SOPA, ACTA and PIPA legislation, as Google and Yahoo appear to be restricting a lot of the content due to these acts (perhaps a minor dictatorship in itself). So far, it has only been possible to find a few books regarding these topics that are not backed by governmental or political bodies and/or are not legislative papers. Also, I believe that books of this nature would indeed be ‘content-controlled’, and so not the full opinion of the author.
However, I did a deeper search and found a book that recognises criticisms of the government-led legislative policies. The book notes that although these policies have been implemented over the past few years worldwide, they are not being enforced in developing countries (Ayoob, 2010). This enables us to question the power of such acts in relation to political state powers of certain countries and furthermore why such countries are being ‘allowed leniency’. Furthermore, acts such as the DMCA have been potentially provided to allow ‘content creators’ to charge for the use of such content on third party sites, potentially damaging and restricting the content on the likes of ‘free’ or non-profit sites such as Wikipedia.
With the Arab Spring appearing towards the end of 2010, many political hacker groups have started to ascend to contribute to state security and governmental systems. These hackers are collaborating with european and american hackers in a fight for digital democracy. The aforementioned film collaborates with these hackers in an appeal to stand-up against political dictatorships and restricting legislative bodies.
In my next post I hope to research the arab spring and hacking in relation to moral philosophy and whether these legislative acts are in motion to restore ‘fairness’ to content creators or whether this is simply an act of restricting freedom of information over the internet.
Ayoob, E. (2010). Recent Development: The Anti-Counterfeiting Trade Agreement. In The Cardozo Arts and Entertainment. LJ.
Management 101 – concepts and definitons no comments
This week I have begun looking at the discipline of management by reading David Boddy’s Management: An Introduction. This book is recommended as a sound introduction to the discipline by many universities, including Southampton and the LSE. In it Boddy (p. 3) outlines the existence of ‘management’ as both a general human activity and as a ‘specialist occupation’. Our focus is on the specialist occupation, which aims to ‘create wealth by adding value to resources, which managers to by influencing others’ (p. 3). Management occurs in organisations, which are defined as ‘social arrangement[s] for achieving controlled performance towards goals to create value’, recognising that the idea of adding value is both subjective as well as relative (pp. 7-8). With the development of such organisation, in historical as well as social terms, the element of ‘management’ is separated from the ‘work’. That is the moment management emerges as a distinct role (p. 10).
Managers influence others in three main ways:
– Through the process of management
– Through the tasks of management
– Through shaping the context
The process:
There are many different aspects of the management role in an organisation. Mintzberg’s research from 1973 shows ten, Boddy highlights more, broadly classified in three categories: informational, interpersonal and decisional, as described in more detail in figure 1. These roles operate simultaneously and are more or less important depending on the level of management and the type of organisation (pp. 15-19).
The tasks:
Figure 2 below is a representation that summarises the four main management tasks of: (pp. 19-22)
– Planning – setting out the overall direction of the work
– Organising – actions the plans by allocating time and resources
– Leading – generate effort and commitment
– Controlling – monitoring progress and reactive accordingly
The context:
Managers can also influence their contexts (internal and external) to achieve their objectives. Figure 3 provides a good illustration.
Here we come to a bit of an epistemological discussion within the discipline of management because there are broadly speaking three schools of thought regarding the relationship between context and actions:
– Determinism – performance depends on external context
– Choice – people are able to influence even shape their context
– Interaction – people are influenced by and in turn influence their context
Boddy concludes this introductory chapter by emphasising the importance of ‘critical thinking’ as a basic skill for managers. He defines as a way of thinking which ‘identifies the assumptions behind ideas, relates them to their context, imagines alternatives and recognises limitations’ (p. 26).
So the discipline is concerned with a specific type of human activity, management. But not the universal activity of managing one’s life, family, etc. but rather a specific role within a specific kind of socio-economic arrangement: the organisation. This has strong implication for the management epistemology and ontology, which I will explore further next week after presenting a number of theoretical models of management.
References
Boddy D. (2010) Management: An Introduction, 5th edition, Harlow: Financial Times Prentice Hall
Limits of Computation no comments
In the second post it was stated that theory of computer science draws great attention to the boundaries of algorithms, to the problems than can or cannot be solved with computational methods. This led me to search for an introductory book on the limits of computation, finding Computation and its Limits by Paul Coockshott (2010).
The book provides a clear explanation of what computation is in its second chapter, along with a succinct historical overview of computational machines (more developed in the third chapter). In this definition, the author raises the question of what is evolutionary and what is cultural when carrying out computing operations. It also illustrates with practical examples how, as humans, we are equipped with physical and mental features to perform certain tasks such as counting, adding, or creating aides for calculation. These two first chapters highlight the importance of mathematics as an underlying element of all sciences, therefore including social sciences, although not explicitly. And this is the core conception that can be extracted from this book in order to find out the epistemological processes of computer science: Complex systems can be broken down into simpler ones, and ultimately understood thanks to the simplicity of maths.
The fourth chapter introduces propositional logic, set theory, and predicate logic. Being familiar to their core concepts may be helpful to social scientists who intend maintain a fluid communication with computer scientists, as logic and set theory seems to be the foundations on which computer science is built.
Although the book is somewhat introductory, some solid background in maths and computer science is required in order to understand what is meant with the limits of computation. However, the reading was not in vain, as it made me come to the realisation that perhaps exploring the boundaries of computation for creating an ‘uncrackable’ voting scheme may be an exclusive task for computer scientists, and perhaps interdisciplinary discussions should take place from different starting points.
Applied Geography no comments
Geographic knowledge skills can be applied to the resolution of social, economic and environmental problems and can be viewed as a socially relevant approach to the study of the relationships between people and their environments. Applied geography is an approach whose reasoning is based on a philosophy of social knowledge and focuses on the application of geographical skills.
There are three principal kinds of science as described by Habermas (1974) and which can also be seen as underpinning the epistemology’s of applied geography.
- Empirical- analytical. The aim of this type of science is to predict he empirical world using scientific positivism.
- Historical-hermeneutic. Interpreting the meaning of the world by examining the thoughts behind the actions that produce the world of experience.
- Realist-emancipatory. Here the aim is to uncover the real explanations governing society and encourage the members of society to seek a superior formation.
These three different types of science all have different goals.
- A positivist scientific explanation is the principal route to knowledge. Its primary goal is to understand, predict and eventually control environmental events. However, complexity has made this impossible to achieve. Such an approach ignores human agency and social structures in decision making. The desire to predict and control events is similar to social engineering, and can be considered ineffective and socially unacceptable.
- The aim is to raise self and mutual awareness. This approach is especially relevant in areas where stereotyping of certain groups and places can lead to social tension, isolation and conflict.
- Realist science seeks to promote real understanding by people of their position within their socio-political structure and of the factors that condition their lifestyles and living environment.
This three fold typology of science as described by Habermas characterises applied geographers as agents for social change. The goal is to enhance human well being through a shared philosophy pursing knowledge in order to resolve social, economic and environmental problems.
From Applied geography : principles and practice : an introduction to useful research in physical, environmental and human geography by Michael Pacione.