Taxonomy of Tagging
After looking at numerous publications and web content over the internet I am going to write the first edition of findings. While we sometimes refer to social tagging systems as a coherent set of applications, it is clear that differences between tagging systems have a significant amount of influence on resultant tags and information dynamics. It is also clear that the personal and social incentives that prompt individuals to participate affect the system itself in various ways. Therefore we can classify the tagging into two taxonomies such as
1. Characteristics of system design and
2. User incentives and motivations may influence the resultant tags in a tagging system
I’ll write about the user incentives and motivations in my later post. For now let’s talk about the Characteristics of system design. The design of the system may solicit tagging useful for discovery, retrieval, remembrance, social interaction, or possibly, all of the above. After reading the literature related to tagging system and the concepts around it, I have used some dimensions that may have direct and considerable effect on the content of the tags. Some of the dimensions are as under:
Tagging Rights:
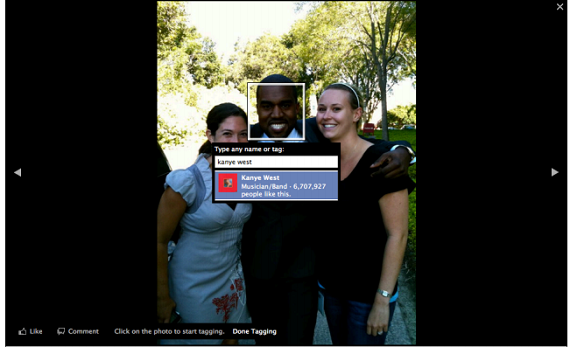
Possibly the most important characterization of a tagging system design is the system’s restriction in certain scenarios. For instance, systems can choose the resources users are to tag (such as images in the ESP Game) or specify different levels of permissions to tag. As of now we are using Facebook integration to authenticate and display the list of user’s Facebook friends Likewise, systems can determine who may remove a tag, whether no one (e.g., Yahoo! Podcasts), anyone (e.g., Odeo), the tag creator (e.g., Last.fm) or the resource owner (e.g., Flickr). At the moment we have given rights to the resource owner and the person who is tagged.
Tagging Support:
According to the categories described by Cameron et al, our system falls in the category of viewable tagging, where the users can see the tags already associated with a resource (photo).
Aggregation:
This attribute is more of a future work thing, where the tags assigned to a particular resource can be used for the accuracy and in determining relationships between users, tags and resources.
Type of Object:
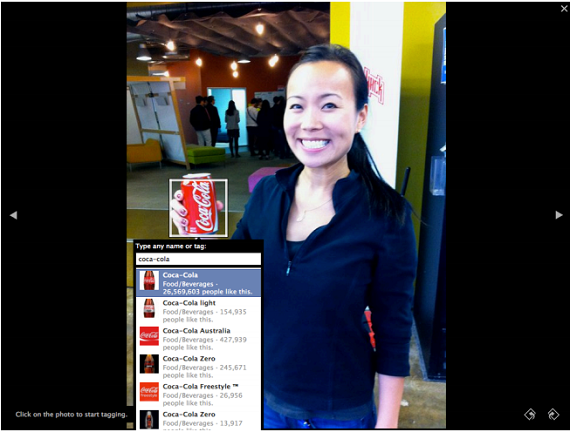
We are focusing on the photos, so images can be tagged wherever they are on a web page. Moreover, people can tag objects e.g a can of coke, this idea is potentially a business/revenue generating idea.
Source of material:
Resources to be tagged can be supplied by the participants (e.g., YouTube, Flickr, Technorati, Upcoming), by the system (e.g., ESP Game, Last.fm, Yahoo! Podcasts), or, alternatively, a system can be open for tagging any web resource (image).