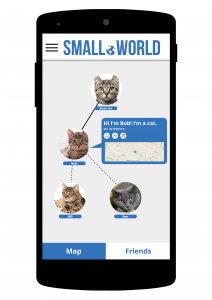
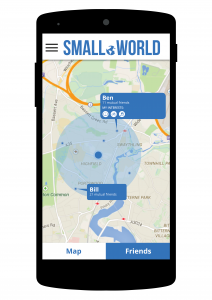
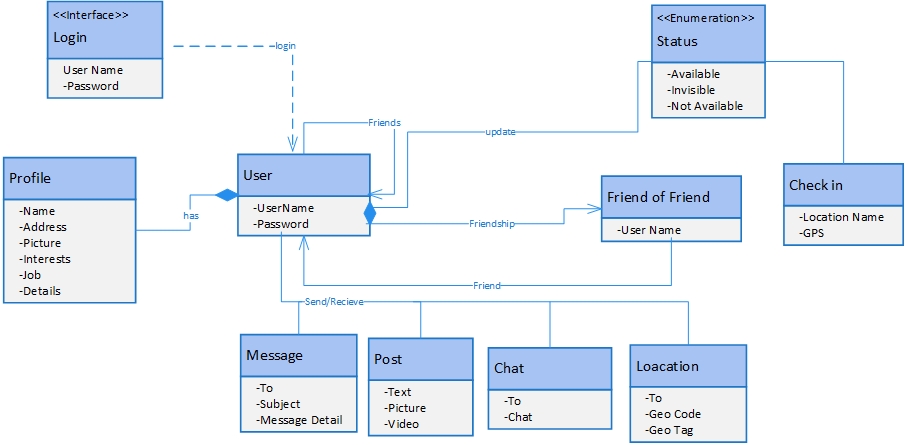
It is really important to create an app that is accessible to the widest possible set of users. Considering that 15% of the world’s population have a disability that affects their access to mobile technology, it is important to make small provisions that can make a huge difference to the user experience of someone with a disability (Narasimhan and Leblois, 2012).
Our app will be published with an Accessibility Statement that will express our commitment to accessibility. An important part of this is allowing a clear and easy way for users to contact us to make suggestions for improvement based on their experiences of using the app (Onevoiceict.org, 2015)
Our app will have the following accessibility features:
- A help section describing how to use the app.
- Ability to alter the text formatting.
- Minimal or no use of red and green together for colour-blind users.
- Simple and consistent design to help users with cognitive disabilities.
- Ability to change the display (e.g. to increase the contrast) for partially sighted users.
Future improvements that could be made include:
- All content on the screen being turned into speech for totally blind users.
- A voice input feature as an alternative to a keyboard for users with upper limb disorders.
References
Narasimhan, N. and Leblois, A. (2012). Making mobile phones and services accessible for persons with disabilities. ITU.
Onevoiceict.org, (2015). First Seven Steps to accessible mobile apps | OneVoice for Accessible ICT. [online] Available at: http://www.onevoiceict.org/first-seven-steps-accessible-mobile-apps [Accessed 27 Apr. 2015].