Rebecca is university of Southampton student. She is aiming to be a Mental Health advisor after finishing her degree. She wants to get an experience as mental health advisor. So, she decides to join “TrustPal”. She logs in using her university email accounts. She edits her profile and interests. Then she clicks on add post and writes, “I like hearing you talk to me”. After talking to a stranger about his sleeping problems. She decides to create a support group for those who are facing sleeping problems. She feels happy when she sees the 5 yellow stars shining on her profile and reads people comments about how helpful she was. And she replies, “ You give me more than I give you. You make me happy and you raise my self-confidence. Thank you”
Author Archives: Mazyounah Alfagham
Scenario 2: Anxiety
It’s Friday afternoon, Nicholas replies “ Happy weekend to you too” in lower voice “It doesn’t seems to be a happy weekend”. He feels persistently unhappy. And he can no longer cope. He decides to go to bed and take a nap. Hoping that the low mood goes away, but it doesn’t. He feels stress even on the free times. He decides to talk to his friend Joe. Joe picks the phone up and starts the call with “Hello drama queen”. He realized it wasn’t a good idea. He remembered that he saw a poster about anonymous chat application called “TrustPal”. He downloads the application. And he logs in using his Soton ID and a nickname. He clicks talk to mentor tap on the application. Natalie (mentor) accept a chat live request from “drama queen” (Nicholas’s nick name). She asks him, after listening to his issue, to take mood assessment quiz in NHS website. Nicholas scored higher than the average degree of anxiety. Natalie gives him a high support. She also provides information about support groups in Trustpal and links to university and NHS services. She asked him to keep in touch. Nicholas feels good when he founds someone who cares about his problem. And he promise Natalie he will be better soon.
Resources:
1.Mood self assessment by NHS http://www.nhs.uk/conditions/stress-anxiety-depression/pages/mood-self-assessment.aspx
2. image reference http://goodmenproject.com
Filed under Scenarios and Personas
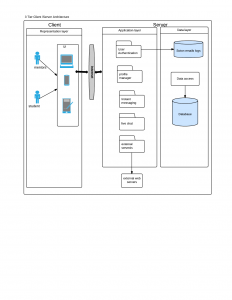
System Architecture
As shown in the above diagram 3 Tier Client /Server Architecture is the proposed solution for our social network
Filed under Overview of standards and protocols
Overview of Standards of Protocols
Our social network provide 3 main features:
- Anonymity
- Instant massaging
- Live chat
– Data anonymization
Our application is based on anonymity, which deals with hidden information such as user’s identity. Even though we ask for university email in the registration, just for verification, system will not store users emails in the database. System will use user nickname to identify users. Even the nickname can be hidden from other users by using “stranger” as identification. In addition, End-to-end encryption will be used to avoid IP identification.
k-anonymity: can be used to personalize application users without compromising individual privacy. Personalization can helps to provide better services and to identify their interest or issues.
-Instant messaging
I2P: is a serverless instant messenger provided by QT software. The main characteristic of this protocol is fully anonymous based instant communication. No server can be between 2 user’s conversations. No ISP can log. No information provide about whom the user chats. It is prevents any node between the two users from having access to the chat. So, I2p is ideal instant messaging solution for our social network. In addition, I2p support file transfer between the two parties.
Extensible Messaging and Presence Protocol (XMPP) can be used as instant messaging protocol for our social network. This protocol is open standard. however, it doesn’t support End-to-end encryption. To overcome this problem, Off-the-Record Messaging (OTR) can be used to provide encryption.
– Live chat
VPchat can be used to support live chat room. VPchat protocol uses a TCP connection.
Session Initiation Protocol (SIP) it is protocol for signaling media streams. This could be used in our social network to support voice call in conjunction with Real-time Transport Protocol (RTP)
References:
- Sweeney. k-anonymity (2002) a model for protecting privacy. International Journal on Uncertainty, Fuzziness and Knowledge-based Systems, 2; 557-570.
- Zantout, B., & Haraty, R. (2011, January). I2p data communication system. In ICN 2011, The Tenth International Conference on Networks (pp. 401-409).
- I2p-bote features [online] http://i2pbote.i2p.us
- Neal, L. (1997, November). Virtual classrooms and communities. In Proceedings of the international ACM SIGGROUP conference on Supporting group work: the integration challenge (pp. 81-90). ACM.
- Rosenberg, J., Schulzrinne, H., Camarillo, G., Johnston, A., Peterson, J., Sparks, R., … & Schooler, E. (2002). SIP: session initiation protocol.
- Frederick, R., Jacobson, V., & Design, P. (2003). RTP: A transport protocol for real-time applications. IETF RFC3550.
- SIP [online] http://www.voip-info.org/wiki/view/SIP
Filed under Overview of standards and protocols
Scenarios and Personas
Purpose:
Scenario that describes the use of an anonymous chat based application for University of Southampton students, which would enable them to chat to mentors, councilors or other students when they have various issues or problems.
Individual:
Jack is a University of Southampton student who is facing a depression after relationship break up.
Natalie is a mentor, working on University of Southampton Mentoring support department.
Layla is a University of Southampton student, who has experienced Jack’s problem before.
Equipment:
Any devices has an Internet connection and “TrustPal” Application.
Scenario:
- Jack, Layla and Natalie (users) can login using their university ID.
- Users identity will be hidden and they will use the system as anonymous.
- Jack can search for keyword “depression” and the system will display all related public posts or support groups.
- Jack can view and add comments to posts.
- Jack can join support groups, which bring together student facing similar issue.
- Jack can ask for virtual consulting and the system will assign the job to a mentor (Natalie).
- Jack can send message to anonymous mentor (Natalie).
- Natalie will receive message from anonymous student asking for help.
- Natalie will provide student with helpful information such as: support groups, university services and NHS services.
- Jack can also ask for online chatting with Natalie.
- Natalie will response and start live chatting with Jack
- After finishing consulting session, Jack can give feedback or rate the mentor.
- Jack found an interesting post about his issue made by another anonymous student (Layla).
- Jack can check Layla statues (online or offline).
- If Layla online, Jack can ask for online chatting.
- Layla can accept or refuse chatting request made by anonymous student (Jack).
- Users can choose their status earthier online or offline.
Filed under Scenarios and Personas
Anonymous Chat applications
| 7cups of tea | Join our anonymous chat room online to talk about whatever is on your mind, friend! Venting to strangers anonymously can really help provide a sense of relief. | http://www.7cupsoftea.com/anonymous-chat/ |
| Stranger meet up | Chat with random strangers online. Pairing up with a random stranger is only one click away. The chat will be completely anonymous. | http://strangermeetup.com/ |
| Anonymous chat | Anonymous chat – the chat for easy communication. | https://play.google.com/store/apps/details?id=ru.dwerty.android.anonymouschat&hl=en |
| Parlor | Talk Anonymous & Meet New People | https://itunes.apple.com/gb/app/parlor-talk-anonymous-meet/id426482708?mt=8 |
Filed under Analysis of existing similar tools