Archive for the ‘Criminology’ Category
Online Identity – Third Post 1 comment
Criminology Focus:
Following last week’s revised Brief, as the literature review has solely been focused on Sociology, it seemed appropriate that the focus this week was turned to Criminology.
This Week’s Achievements:
Last week I aimed to obtain three specific books; however, although I do intend to read all of the recommended textbooks, I decided this week to focus on:
Jewkes, Y. and Yar, M, (eds) ‘Handbook of Internet Crime,’ (Willan Publishing, Devon, 2010)
This textbook is extremely insightful into how the Web has impacted on individuals’ digital expression of their identity. Furthermore, how this may facilitate crime.
Chapter 14 – Smith, R.G, ‘Identity Theft and Fraud’ is particularly relevant, as Smith proposes that “arguably, one of the most pressing financial crime problems that has faced developed societies in recent years – namely the commission of crime through the creation and use of misleading and deceptive identities.” (p273) Therefore, this chapter covers a range of issues relating to identity that has been facilitated by the Web, from the possibility that Avatars can commit virtual crimes untraceable in the real-word, to identity theft – particularly on social networking sites.
Alongside this I thought it would also be useful to obtain some textbooks that are centred on the methodology that underpins the discipline of Criminology.
1) Harrison, J, Harrison, O, Martin, E. and Simpson, M, ‘Study Skills for Criminology,’ (SAGE Publications, London, 2005)
This book was written by academic criminologists targeting people considering or enrolled on an undergraduate degree in Criminology, to enable them to better understand what the course entails and its general requirements. Some areas covered, such as examination strategies are obviously irrelevant to this review; however the book does provide some important insights into the main study skills involved.
2) Babbie, E. and Maxfield, M, G, ‘Basics of Research Methods for Criminal Justice and Criminology,’ (Thompson: Wadsworth, Canada, 2006)
This book is useful as it offers a different view of the methodology used by criminologists, as it is written for individuals undertaking research in the discipline. Therefore, it explains how the elements of ‘Criminal Justice Enquiry’ work, including references to: how data may be collected; how data may be modelled; where criminological theory fits in; and survey research.
Next Week’s Aims:
It would be interesting next week to also find textbooks that are focused on explaining the methodologies that sociologists utilise in their research. Furthermore, reading the other two recommended textbooks is also a priority.
Sociological Theories of Crime and Criminological Psychology no comments
Source: The Oxford Handbook of Criminology (3rd Ed.) by Maguire, Morgan and Reiner
Chapter 2. Sociological Theories of Crime
This chapter provides a broad summary of the various sociological theories of crime which seek to examine the relationship between crime and society.
Anomie theories
Robert Merton’s theory of anomie is caused as a socially-fostered state of discontent and deregulation that generated crime and deviance as part of the routine functioning of a society which promised much to everyone but denied them equal access to its attainment .
In a society where failure is interpreted as personal rather than social weakness, where failure tended to lead to guilt rather than political anger, the pressure to succeed may be so powerful that it impelled people thus disadvantaged to bypass legitimate carers and take illegitimate careers.
Control theory
To control those who seek to commit crime because it’s “profitable, useful or enjoyable” and will certainly break the law if they have to. Travis Hirschi believes the question is not “why do they do it” but should be – “why don’t we do it?”
Four chief elements were held to induce people to comply with rules:
- Attachment – a person’s sensitivity to the opinions of others
- Commitment – investment of time, energy and reputation in conformity
- Involvement – engrossment in conventional activity
- Belief – mirrors a person’s conviction that he or she should obey legal rules
Steven Box’s list of variables that were held to affect control:
- Secrecy (the delinquent’s chances of concealment)
- Skills (knowledge and techniques needed for the deviant act)
- Supply (access to appropriate equipment)
- Symbolic support (the endorsement offered by accounts available in the wider culture)
It is believed that the greater the access to each of the above, the greater the likelihood to commit crime.
Signification
Symbolic interactionism and phenomenology (labelling theory) which insists that people do not and cannot respond immediately, uncritically, and passively to the world “as it is”.
Deviance itself was to become more generally likened to a moral career consisting of interlocking phases, each of which fed into the next, each of which presented different existential problems and opportunities; each of which could distinctively mould the self of the deviant. Not every phase was inevitable or irreversible and deviants could often elect to change direction.
Relevance to the cybercrime
The pressure to succeed in the world today is indeed overwhelming and it is obvious that some will be prepared to gain success through illegitimate ways, as proposed by Robert Merton. Obviously, in the age of the internet, the faster way to gain success would be to exploit the internet platform as it gives the offender potential access to multi-millions of connected users all across the globe. In fact, when compared with Steven Box’s list of variables, it becomes obvious why cybercrime occurs. A high degree of secrecy (ignoring the technical details) can be achieved over the internet with little skill required since a lot of the techniques are well published. Supply to equipment is easy since all one needs is a computer whilst there is a symbolic support in the sense that cybercriminals are always portrayed as smart and cool. Such a sequence of steps to commit a cybercrime is also described in symbolic interactionism and phenomenology that each step feeds into the other but each step is not irreversible nor inevitable.
Chapter 5: Criminological Psychology (Forensic Psychology)
In this chapter, the authors attempt to bring forward to the reader some of the few behavioural and cognitive criminological theories.
Differential Association Theory
Sutherland proposed that criminal behaviour is in fact a learned behaviour. He speculated that learning occurs in close social groups and hence behaviour is acquired through such contacts.
Product of learning is not just the skills of committing crime but also the attitudes that outweigh conformist attitudes and so are conducive to breaking the law.
Differential Reinforcement Theory
The theory of differential reinforcement theory: a criminal act occurs in an environment in which in the past, the actor has been reinforced to behaving in this manner, and the aversive consequences attached to the behaviour have been much of such a nature that they do not control or prevent the response. (Hence, the individual’s history of reinforcement and punishment can be used to explain his/her criminal behaviour.
Personality and Crime
Eysenck’s theory seeks to offer an explanation of crime based on an interaction of biological, social, and individual factors. He proposed three dimensions of personality: extraversion (E), neuroticism (N) and psychoticism (p). He saw E, N and P as a continuum in which the majority of the people fall in the centre of the continuum. He believes and empirically proven that offenders demonstrate high N, P and E scores.
Cognition and Crime
Kohlberg argues that offending is associated with a delay in the development of moral reasoning : when the opportunity for offending presents itself, the individual does not have the reasoning that would allow him or her to control and resist temptation.
Empiracal proof (Blasi 1980, Nelson, Smith and Dodd 1990) that offenders do typically show lower levels of moral reasoning.
Social problem solving skill:
- To understand the situation
- To envisage potential courses of action
- To consider and evaluate the outcomes that might follow the various actions
- Finally to decide on a course of action and plan its execution to achieve a desired outcome
Again, there is empirical proof that offenders (both male and female) give less socially competent responses to social problems.
The reasoning criminal
Personal benefit is the primary motivation of crime and in pursuit of personal gain, individuals make decisions and choices that are more/less rational in nature.
Social factors, including family/peer group, play a background role in an individual’s development in growing up with an association with crime. However, the rational “event decision” at the point of committing the offence is predominant.
Frequency of crime is associated with increased opportunity and when confronted with opportunity, offenders do make rational choices about their behaviour
Relevance to cybercrime
It would be interesting to attempt to study the psychological characteristics of cybercriminals to see whether Eysenck’s theory holds in cybercrime and whether their moral reasoning and social problem solving skills are lacking. Also, whether cybercriminals are reasoning criminals is difficult to conclude because the scale of crime could be so great that it would be difficult to envisage the consequence of committing a cybercrime.
Online Identity – Second Post no comments
Revised Brief:
This week I have revised my original Brief to observe the concept of ‘online identity’ from both a sociological and criminological perspective. Unfortunately, there was little information to be found on this area from a political view, thus this subject has been discounted.
The area of Criminology poses very interesting research questions in regards to the concept of online identity. In particular how anonymity online could be potentially used by individuals perpetuating criminal activities. This varies from individuals pretending to be reputable organisations, perhaps asking for bank details or other personal information; to sex offenders being able to use particular online identities, different from their real-world self, to groom children. How criminals may manipulate and use online identity is quite fascinating.
This Week’s Achievements:
This week I have focused my reading on two Sociology textbooks:
1) Sassen, S, ‘A Sociology of Globalization’ (W.W. Norton & Company Inc, London, 2007)
This book, although not particularly relevant to the concept of online identity, was useful when considering how the Web has affected society on a global scale; perhaps helping to underpin the concept of globalisation. However, this book is also valuable in illustrating the basic principles of sociological methodology, which seems in this instance to be built upon different studies and statistics produced by a variety of sociologists in a particular area.
2) Nunes, M, ‘Cyberspaces of Everyday Life,’ ( University of Minnesota Press, London, 2002)
This book offers a socio-cultural view on the Web and various aspects of online identity. From how identity is used in online e-Learning, such as the University of Phoenix, where many individuals use pseudonyms instead of real names; to websites that seems to allow the expression of one part of a user’s identity, such as a parenting website. Nunes argues on this parenting website users’ identity does not seem to go beyond the realms that they are parents, anything else about identity is irrelevant. Furthermore, this book offers interesting insights into how online identity may be free from: gender, race, sexuality and social-class, and how in turn this may impact on social interaction.
Next Week’s Aims:
After contacting the School of Social Sciences in regards to issues surrounding the concept of identity on the Web, the following textbooks were kindly recommended:
- Muncie et al, ‘Criminological Perspectives’ (2nd edit.,) – used at level two for Criminology.
- Yvonne Jewkes and Majid Yar, ‘Handbook of Internet Crime’ – contains chapters relevant to the issue of identity.
- Giddens, ‘A Sociology’ – provides a good overview of Sociology (used by undergraduate sociologists)
Therefore, next week my aim is to have found these three textbooks in Hartley library and to create a short summary about each.
The Criminology and Economic incentives behind Cybercrimes no comments
The prevailing assumption of cybercrime is that it is a massive threat that could cause unimaginable chaos to society. However, this is just a virtual threat. The reality is that cybercrimes most often involve small impact bulk victimisations which can be individually insignificant but collectively significant. Most cybercriminals target the long tail of crime where they prefer to commit more crimes with less gain. An example of that would be a cybercriminal scamming 50 million people for £1.
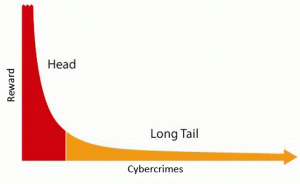
Such a model of crime has several advantages over traditional models of crime as individually insignificant amount of losses means:
1. Victims would be less bothered about reporting the crime
2. Police less likely to get involved
3. Credit card companies less bothered
For more information, please see the presentation on “Organized Crime and the Organization of Cybercrime” given by David Wall.
The study of cybercrime requires a multidisciplinary approach as the society is affected. Economics, law, sociology, psychology and criminology are just some of the disciplines involved. It is my intention to understand cybercrimes from the economics and criminology perspective so that I can have a better understanding on why cybercrimes occur.
Economics
After reading the presentation on “How Economics and Information Security Affects Cyber Crime and What This Means in the Context of a Global Recession” given by Peter Guerra, I believe that by understanding more about the economic incentives behind cybercrime, that is, the incentives to commit crime and the incentives to protect from crime, I would gain a better understanding of the rationale behind cybercrimes and whether critical points can be identified using economic theories.
The economic books which I’m proposing to read are:
- Microeconomics: Principles and analysis by F.A. Cowell
- Economics (6th Ed) by J. Sloman
Criminology
Criminology is the study of crimes and by studying criminology, I’m looking to develop an understanding on the theories in criminology and an imaginative mind on crimes so that not only I can understand why crimes occur but can also anticipate when and where crime is likely to occur. There are three textbooks I’ve found which are relevant:
- Criminology: The Basics by Sandra Walklate
- The Oxford Handbook of Criminology by Mike Maguire, Rod Morgan, and Robert Reiner
- Cybercrime: The Transformation of Crime in the Information Age by David S. Wall
- Handbook of Internet Crime by Yvonne Jewkes and Majid Yar